data feed
What is a data feed?
A data feed is an ongoing stream of structured data that provides users with updates of current information from one or more sources. A data feed can stream continuously or be delivered on demand. Data feeds make it possible to have new content or updates delivered to a computer or mobile device as soon as it is published. The same technologies are also used to supply data to other software.
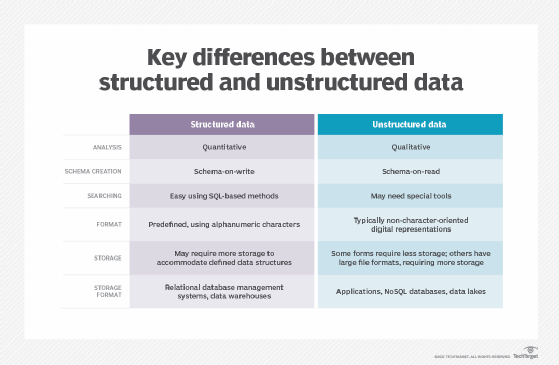
A data feed is an online mechanism for sending up-to-date data or content to users, either automatically or in response to users' demands. This data is usually structured and sent from a server to a specific destination, such as a website or mobile phone app.
There are many types of data feeds, including news, weather and sports updates, content publication feeds, and social media timelines. In a security context, threat intelligence feeds provide organizations with constantly updated information about potential or current attacks that could pose a risk to their business.
Data feeds are often described in terms of their methods of delivery. Really Simple Syndication (RSS) feeds, for example, use an Extensible Markup Language (XML) file format to deliver content from multiple sources to users. An RSS aggregator or RSS reader allows the user to see summaries of all their feeds in one place. Atom, an alternative, open source specification, provides similar functionality, meaning that it enables content creators to syndicate their information and allows users to view content from different sites in a single operation.
Examples of data feeds
RSS feeds are one of the most common types of data feeds. Websites and blogs use the RSS mechanism to automatically send information such as notifications and article excerpts to users so that users don't have to visit each site separately. Only those users who subscribe to the RSS feed receive the site's -- and other sites' -- notifications.
Facebook's Feed, formerly known as News Feed, is another popular example of a data feed. Introduced in 2006, Feed pulls items from status updates, photos, videos, links, app activity and likes from people, pages and groups that the user follows. Feed makes it easier for Facebook users to explore new content. This content might relate to new posts, profile changes, friends' birthdays, upcoming events and other updates that are deemed useful to the user by Facebook's algorithms. Items in Feed can be self-contained or summaries that include links to further information.
Other social networks such as X -- formerly known as Twitter -- Instagram and Pinterest also use data feeds to display up-to-date content to users. As with Facebook, the data feeds on these sites are also customized for each user and typically include a mix of content, such as new posts and suggestions related to other posts, photos and accounts the user might choose to look at or follow.
What is a product feed?
A product feed is another example of a data feed that is particularly important in the context of e-commerce. Product sellers make their product data feeds available to e-commerce websites such as Amazon.
A product feed refers to a file that lists all the seller's products as well as product attributes, offers, descriptions and information such as features, material, size, etc. The seller can provide the file in a variety of formats, such as XML, comma-separated values or JavaScript Object Notation. Some e-commerce platforms also support plain text product feed files.
The product feed file typically includes many columns and rows, with each column specifying some information about the product, such as its name, SKU number, color, price and availability. The more structured information that's included in the file, the more detailed the product feed, and the more information that's available to consumers visiting the e-commerce website.
Sellers either create the file manually or by using a feed creation tool. Regardless of the method used, the feed file makes it possible to display information about the seller's products on the site. By providing the file to the site, sellers increase their chances of selling their products. A well-optimized and updated product feed also allows them to attract more potential buyers and increase conversions and sales.
What is a product data feed in Google Ads?
Like social media sites, search engines such as Google use data feeds to display customized and relevant ads to users. Before creating and posting ads for different campaigns to Google Ads, advertisers must provide and manage all their data feeds -- or data sources -- for ads, assets and targeting. They must also upload ad customizers, which are the parameters required to adapt the ad text to the context of a user's search or website being browsed. Advertisers can also create a dynamic ads feed, which functions as a product inventory that is then sourced to create ads on Google Ads.
Why are data feeds important?
A data feed is a good way for content creators and publishers to keep their target audience engaged with their content. For example, through RSS feeds, bloggers can send notifications about their latest blog posts to their subscribers to help increase traffic to the blog. Subscribers can click on the notification links to view the new posts.
Social media websites also use data feeds to persuade users to stay on the site and continue to engage with its content. Furthermore, feeds are often used to show targeted ads to users based on their activity history, profile information or interests. Customized ads increase the probability that users will find them relevant and make purchases.
Product data feeds on shopping websites enable users to find products. An accurate product data feed helps to ensure that products are accurately linked to user searches. It also allows users to make informed purchase decisions based on the information displayed on their browser or in the application they're using.
Explore the steps to turn real-time data streams into business value. Find out how streaming analytics can provide insight and value to your organization. Learn about using threat intelligence to protect corporate assets in "Threat Intelligence Frameworks to Bolster Security."