
data loss prevention (DLP)
What is data loss prevention (DLP)?
Data loss prevention (DLP) -- sometimes referred to as data leak prevention, information loss prevention and extrusion prevention -- is a strategy to mitigate threats to critical data. DLP is commonly implemented as part of an organization's plan for overall data security.
Using a variety of software tools and data privacy practices, DLP aims to prevent unauthorized access to sensitive information. It does this by classifying the different content types within a data object and applying automated protection policies.
A multilayered DLP strategy ensures sensitive information remains behind a network firewall. Creating a DLP plan also enables an organization to review and update its data storage and retention policies to maintain regulatory compliance.
The work-from-home trend, coupled with more sophisticated cyber attacks, underscore the growing interest in DLP. Research firm Gartner estimated that 90% of organizations implemented at least one form of integrated DLP in 2021, up from 50% in 2017.
This article is part of
What is data security? The ultimate guide
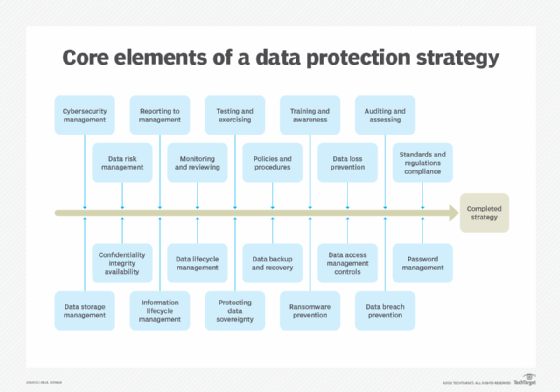
How does data loss prevention work?
DLP software monitors, detects and blocks sensitive data from leaving an organization. That means monitoring both data entering the corporate networks, as well as data attempting to exit the network.
Most DLP software products focus on blocking actions. For example, if an employee tried to forward a business email against company policy outside the corporate domain or upload a corporate file to a consumer cloud storage service such as DropBox, permission would be denied.
Also, DLP software can block employee computers from reading and writing to USB thumb drives to prevent unauthorized copying.
Detection primarily centers on monitoring incoming email, looking for suspicious attachments and hyperlinks for phishing attacks. Most DLP software offers organizations the option of flagging inconsistent content for staff to manually examine or block it outright.
In the early days of DLP, security teams set the rules around detection and blocking, but those were simplistic and often circumvented. Newer software uses machine learning-based artificial intelligence, which can learn and improve the approach to detection and blocking over time.
Why is data loss prevention important?
Data loss can result in hefty fines and possibly criminal penalties. It also can negatively affect an organization's business and even put it out of business.
In 2017, the personal and financial information of nearly 150 million people was stolen from an unpatched Equifax database. The company failed to fix the vulnerability promptly, then failed to inform the public of the breach for weeks after it was discovered. In July 2019, the credit agency was fined $575 million.
Data loss could cause executives to lose their jobs. Top execs at Target and Equifax resigned following major data breaches that hurt their companies and cost them millions in fines.
If the fines don't kill a business, the loss of customer and public faith well might. A 2019 report by the National Cyber Security Alliance, based on a Zogby Analytics survey of 1,006 small businesses with up to 500 employees, found that 10% of companies went out of business after suffering a data breach, 25% filed for bankruptcy and 37% experienced a financial loss.
What are the types of data loss prevention?
Network DLP covers a range of data security techniques. These include the following:
- Data identification. DLP is only useful if it is told what is and is not sensitive. Businesses should use an automated data discovery and classification tool to ensure reliable and accurate identification and categorization of data rather than leaving it to humans to decide.
- Protecting data in motion. Data is moved around quite a bit internally, and external breaches often rely on this to reroute the data. DLP software can help ensure that data in motion is not routed someplace it should not go.
- Protecting data at rest. This technique secures data when it is not moving, such as residing in databases, other apps, cloud repositories, computers, mobile devices and other means of storage.
- Endpoint DLP. This type of DLP functionality protects data at the endpoint device level -- not just computers, but mobile phones and tablets as well. It can block data from being copied or encrypt all data as it is transferred.
- Data leak detection. This technique involves setting a baseline of normal activity, then actively looking for unusual behavior.
- Cloud DLP. DLP solutions have evolved to manage and protect critical data in software-as-a-service and infrastructure-as-a-service applications.
Common trends and reasons for DLP adoption
A 2022 Gartner report found that 35% of all DLP implementations fail. Such failure can lead to severe consequences for a business, including fines, penalties and degraded reputation. It's these types of factors that drive DLP adoption, including the following:
- Cost. The average total cost of a data breach was $4.2 million in 2021, a 10% increase from 2020, according to an IBM and the Ponemon Institute report.
- Compliance. Expanding global regulations heightens the need for DLP to satisfy expansive laws and requirements on data governance.
- Data volume. Companies produce more data than ever, and the data generates a great deal of value. Sophisticated hackers are on the prowl to find ways to steal data for profit, including identity theft, insurance fraud and other economic crimes.
- Emergence of the chief information security officer (CISO). Companies are hiring professional security specialists such as CISOs to craft governance policies to secure intellectual property and other proprietary information. DLP is typically a significant part of efforts.
- Talent shortage. Skilled data security professionals are in high demand and difficult to find. To compensate, organizations often outsource DLP to vendors that provide managed IT services.
- Wider attack surface. Cloud services, endpoint devices and third-party vendor tools are potentially vulnerable to ransomware and other cybersecurity threats.
Data loss prevention best practices
Organizations can take several steps to implement a DLP program, including the following:
- Conduct an inventory and assessment. Businesses can't protect what they don't know they have. A complete inventory is a must. Some DLP products -- from vendors such as Barracuda Networks, Cisco and McAfee -- will do a complete scan of the network.
- Classify data. Organizations need a data classification framework for both structured and unstructured data. Such categories include personally identifiable information (PII), financial data, regulatory data and intellectual property.
- Establish data handling and remediation policies. The next step after classifying the data is to create policies for handling it. This is especially true with regulated data or in areas with strict rules -- such as Europe with GDPR and California with CCPA.
- Implement a single, centralized DLP program. Many organizations implement multiple DLP plans across different departments and business units. This leads to inconsistency of protection and the lack of a full picture of the network. There should be one overarching program.
- Educate employees. Unintended actions are far more common than malicious intent. Employee awareness and acceptance of security policies and procedures are critical to DLP.
Data loss prevention tools and technologies
There are two types of DLP products: dedicated and integrated.
Dedicated are standalone products that are in-depth and complex. Integrated products are more basic, work with other security tools regarding policy enforcement and are less expensive than dedicated DLP tools.
DLP software products use business rules to enforce regulatory compliance and classify and protect confidential and critical information. This means unauthorized users cannot accidentally or maliciously share data that poses an organizational risk.
It's doubtful one tool will meet all of an organization's data loss prevention needs. Many DLP vendors have one area of focus, while others have suites of tools that fit together. Businesses can assemble a set of best-of-breed tools or use an all-in-one suite.
Some of the premier vendors include the following:
- Broadcom's Symantec Data Loss Prevention. This enterprise-level DLP software covers endpoints, data center and cloud computing.
- Check Point Data Loss. This tool focuses on breaches and data exfiltration.
- CoSoSys Endpoint Protector. This is a dedicated all-in-one protector for Windows, Apple and Linux.
- ManageEngine Device Control Plus. This is a dedicated endpoint protector focused on USB security.
- McAfee Total Protection for DLP. This is a suite of six DLP products for discovery, monitoring and prevention.
- SolarWinds Data Loss Prevention with Access Rights Manager. Despite the massive security breach, SolarWinds is widely viewed as one of the best DLP providers out there.
- VikingCloud Endpoint Protection. This product focuses on insider risk, such as data theft and unauthorized internet use.
Learn more about specific data loss prevention tools.