virtual hard disk (VHD)
What is a virtual hard disk (VHD)?
A virtual hard disk (VHD) is a disk image file format for storing the entire contents of a computer's hard drive. The disk image, sometimes called a virtual machine (VM), replicates an existing hard drive, including all data and structural elements. It can be stored in any location accessible to the physical host, and it is also transportable, meaning it can be stored and moved with a USB flash memory device.
Virtual hard disk vs. physical hard disk: Similarities and differences
A virtual hard disk has similar functionality to a physical hard disk drive. For example, it often contains the same hard drive sectors, such as a file system, disk partitions, etc. It also appears and operates like a hard disk that's physically connected to the system. Like a hard disk, the VHD can do the following:
- create disk sectors, files and folders
- run an operating system
- execute user applications
What differentiates the VHD from a physical hard disk is that it is designed for use by virtual machines and is installed on a virtual machine infrastructure, most commonly VMware Workstation and Hyper-V VMs.
While a VHD is created on a physical hard drive, it is a "virtualized" file and has its own logical distribution. Its disk size can be fixed or flexible. This size is managed by the operating system (OS) or virtualization manager.
The OS communicates with the device drivers to access the VHD.
Types of virtual hard disk
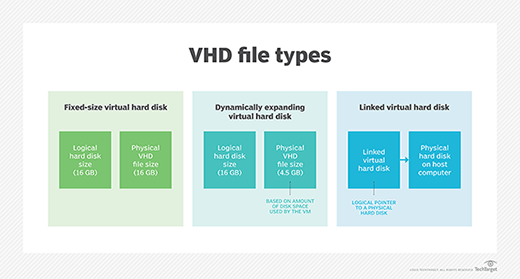
The main types of VHD formats are fixed, dynamic and differencing virtual.
Fixed virtual hard disk
In this VHD format, the VHD consumes a fixed amount of space on the host machine hard disk drive. Fixed VHDs support fast processing speeds and constant fragmentation.
Dynamic virtual hard disk
This VHD format has a varying disk size. The storage space starts at a particular minimum size and grows as data is added to the VHD. Its main advantage is that it speeds up storage space allocation.
Differencing virtual hard disk
A differencing VHD is used to create a copy of an existing disk. Two VHDs are used, a parent and a child. With a differencing VHD, it is possible to make changes to a parent VHD without altering that disk.
Benefits of virtual hard disk
Following are some benefits of using a VHD:
Easy deployment. A VHD has provisions for pre-built and standard configurations in the VHD files for working on specific operating system environments, which simplifies deployment.
Efficient backup and restore. If VHD data is accidentally deleted or affected by a malicious file injection, it can be recovered.
Snapshot recovery. A snapshot of an existing VHD configuration can be recovered, allowing a user to revert to a previous stage if there are installation problems and troubleshooting doesn't offer any fixes.
Swift replication. The work or file in one system can be replicated to another system. This is especially useful for developers who collaborate.
Isolation for users. Users can work on their chosen OS without interference from other users.
Cost-effectiveness. VHD eliminates the need for multiple hardware components and OSes, reducing the cost of storage and deployment.
Process to create a virtual hard disk in Windows
In Windows operating systems (8.1, 10, 11, Server 2016, Server 2012 R2, Server 2012), VHDs appear like physical disks in Disk Management utility. When a VHD is attached, it appears blue. If it is detached, the icon turns gray.
Steps to create a VHD
Admin access is required to do the following:
- On the Action menu, select Create VHD.
- The Create and Attach Virtual Hard Disk dialog box opens.
- Specify the location on the physical computer where the VHD file will be stored, and the size of the VHD.
- In Virtual hard disk format, select dynamically expanding or fixed size.
- Click OK.
How to attach a VHD (i.e., make it available for use)
- On the Action menu, select Attach VHD.
- Specify the VHD location.
How to detach a VHD
- Right-click the disk.
- Select Detach VHD.
- Click OK.
Detaching a VHD does not delete the VHD or its data. It simply makes it unavailable and removes it from use.
VHD vs. VHDX
The VHD file format was originally introduced with Connectix Virtual PC, and was eventually adopted by Microsoft Hyper-V. It works with many versions of Microsoft's Windows OS.
VHDX is functionally equivalent to VHD. However, it is an advanced version of VHD that supports larger storage capacity, larger logical sectors and live disk resizing. VHDX also provides the following advantages over VHD:
- metadata updates tracking;
- data protection against power failures;
- more adaptable to newer hardware; and
- support for custom metadata.
Despite these differences, both VHD and VHDX disk images are prone to file system corruption. This could be due to corrupted hard disk storage, suboptimal network conditions during file transfers or interference from antivirus programs. If a VHD or VHDX file is corrupted, a recovery tool can help recover some or all data.
See also: What types of VHD files does Hyper-V support?, what are the benefits of using the Boot to VHD feature?, PowerShell commands and other methods to resize VHDs and resizing a VHDX file without missing a beat. Explore: Can you create a dynamically expanding virtual hard disk?, set up a virtual hard disk and perform a Windows 10 dual boot and setting up virtual hard disk storage.







