digitization
What is digitization?
Digitization is the process of converting analog information into a digital format. In this format, information is organized into discrete units of data called bits that can be separately addressed, usually in multiple-bit groups called bytes.
This is the binary data that computers and many devices with computing capacity, such as digital cameras and digital hearing aids, can process.
How is information digitized?
Information is digitized through a process called encoding, which converts analog signals into a digital format.
Digitizing information typically involves one or more of the following processes:
- Scanning. Using a scanner to capture an image, which can be an image of text, and convert it to an image file, such as a bitmap.
- Optical character recognition. An OCR program analyzes a text image for light and dark areas to identify each alphabetic letter or numeric digit, and converts each character into an ASCII code.
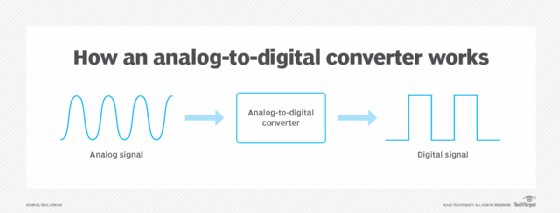
- Recording. Capturing a sound or image on a recording medium, such as magnetic tape or disks, and converting it using an analog-to-digital converter.
- Sampling. Sampling measures the amplitude, or signal strength, of an analog waveform at evenly spaced time markers and represents the samples as numerical values for input as digital data.
- Audio and video digitization. Digitization converts analog audio and video recordings into digital formats, enabling digital storage, editing and playback. This includes digitizing music, speeches, interviews, movies, TV shows and webcam footage.
- Data digitization. Numeric data can be digitized by converting it into a digital format. This enables easier storage, processing and analysis of the data. Data digitization is commonly used in fields such as scientific research, finance and weather forecasting.
The history of digitization
Digitization gained popularity in the late 20th century with the advent of PCs and the internet. These technologies made it possible to convert many different forms of information -- including text, images, audio and video -- into digital formats.
Some key milestones of digitization include the following:
- 1950s. With the evolution of computers, a variety of data formats were converted into computer-friendly 1s and 0s, marking the beginning of digitization. This paved the way for the digitization revolution. In 1956, IBM introduced random access data and magnetic disks with their 305 RAMAC and 650 RAMAC computers. These systems included the 350-disk storage unit, which weighed one ton and had a total capacity of 5 megabytes. It was originally used in the United Airlines reservation system.
- 1960s. The pulse-code modulation technique, which produces a series of numbers in binary form, marked the beginning of the development of digital audio recording technology in the 1960s. Image digitization was made possible with the development of the first digital computer-based image scanner in the late 1960s.
- 1970s. Digital storage became more widely available to the general public with the advent of PCs and the internet.
- 1980s and 1990s. The expanding use of the internet and the acceleration of digital technology in the consumer market accelerated. These technologies made it possible to convert different types of information -- such as text, images, audio and video -- into digital formats.
- 2000s and 2010s. With the growth of digital media players, wireless phones and internet streaming services, digital technology continued to be widely adopted. With the introduction of e-books and online publications, text digitization also increased in popularity.
In the present day, the process of digitization is creating greater opportunities for automation and continues to revolutionize communication, commerce and every aspect of modern life. Especially in the last decade, the rise of digitization has been heavily dependent on newer digital technologies, including cloud computing, machine learning, artificial intelligence (AI), internet of things (IoT) and business intelligence.
Examples of digitization
The following are some common examples of information that can undergo digitization:
- Text, such as books, articles and contracts.
- Images, such as photos, artwork and medical images.
- Audio, such as music, speeches and interviews.
- Video, such as movies, TV shows and webcam footage.
- Data, such as numeric data from sensors, financial data and weather data.
- Data from barcodes and quick response (QR) codes can be scanned into a digital format to make them machine readable.
The benefits of digitization
Aside from making information more shareable and easier to access, there are other reasons a business might decide to digitize. Common benefits and use cases of digitization include the following:
This article is part of
What is digital transformation? Everything you need to know
- Ease of access. Digital information can be easily stored, accessed and shared. This is especially important in today's business world, where information needs to be quickly and easily accessible by employees, customers and partners.
- Easy data analysis. Digital information can be manipulated more easily than analog information. This means businesses can more easily analyze and use data for better decision making.
- Improved customer experience. Digitization enhances the customer experience through various means such as chatbots, social media, automated ticketing systems and knowledge bases. This helps resolve customer issues more effectively and efficiently.
- Digital libraries and archives. Digitizing books, manuscripts, historical documents and cultural items increases accessibility to these resources while preserving them for future generations. A wider audience might access these items more easily because of digital libraries and archives.
- Education and online learning. Due to the availability of e-learning resources, remote learning opportunities and interactive digital tools, digitization has made individualized learning experiences and online assessments easier.
- Increased operational efficiency. Businesses can streamline procedures and automate jobs through digitization, resulting in shorter response times and increased productivity. This enhances the overall efficiency of business operations.
- New markets. Businesses can use digitization to expand their consumer base and enter new markets by using the internet and various technology platforms to connect with a global audience.
- Digital transformation in industries. Digitization plays a key role in driving digital transformation initiatives across various industries and supply chains. For example, in the manufacturing sector, it facilitates the creation of smart factories and enables the integration of IoT devices for real-time monitoring and optimization. In the healthcare industry, digitization enhances patient records management, telemedicine service delivery and the ability to monitor patients remotely.
- Reduced costs. Digitization can help businesses save money by reducing the need for paper documents and other analog materials.
The key to a successful enterprise digital transformation is a strong understanding of the desired business goals. Once an organization understands these goals, it can select the right digital technologies and partners to help digitize the business.
The disadvantages of digitization
While digitization offers various benefits, it also comes with some downsides. Common disadvantages of digitization include the following:
- Privacy concerns. Digital information can be easily copied and distributed without the permission of the copyright holder. This has led to problems with piracy and intellectual property theft.
- Data alterations. Digital information can be easily altered or deleted. This can result in errors and misunderstandings, especially if the altered information is not properly labeled or identified.
- Dependence on technology. Digitization can lead to a reliance on technology, which can be expensive and difficult to maintain at scale. If a business's digital systems fail, it's difficult to recover the lost data.
- Upfront costs. Adopting digitization can have upfront costs, especially for those organizations that need to convert large amounts of paper documents into digital data.
- Security risks. The process of digitizing involves storing data and documents digitally, which can raise the risk of security lapses involving sensitive information.
- Digital divide. Not everyone has equal access to digital technologies or the abilities needed to use them. This may lead to a digital divide, where some people or communities might not have as much access to digital information.
Digitization vs. digital transformation
Digitization and digital transformation are related concepts. However, it's important to note that digitization is only one aspect of digital transformation.
- Digitization is the process of converting analog information into binary code -- 0s and 1s -- so it can be stored, processed and transmitted by computers. This process is centered around generating a digital representation of tangible objects or features. An example of digitization is the scanning of a physical document and saving it as a digital file, such as a PDF.
- Digital transformation is the process of using digital technologies to create new or improved business processes, products and services. This holistic process requires a strategic approach that considers the overall goals of the business, as well as the specific needs of customers and employees. It also requires a commitment to change from leadership and a willingness to invest in new technologies and digital processes.
Unlock the key to business survival with a successful digital transformation. Follow our comprehensive template to build a digital transformation roadmap.