domain
What is domain?
Specific to the internet, the term domain can refer to how the internet is structured, and domain also refers to how an organization's network resources are organized. In general, a domain is an area of control or a sphere of knowledge.
What is an internet domain?
An internet domain is an administrative structure for organizing, delivering and accessing services on the internet. The terms "domain" and "domain name" are often used interchangeably (in context of the internet) because the domain structure is associated with how domains are named.
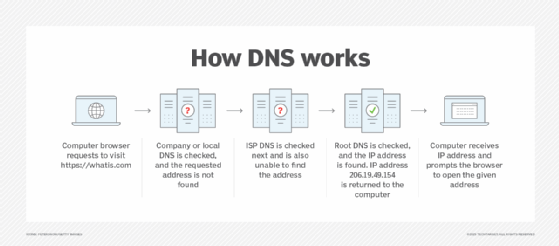
Internet domains are set up in accordance with the Domain Name Service (DNS), an application layer protocol and service used on networks to translate host names to their associated IP addresses. DNS is an essential component of the internet. It is implemented as a decentralized, hierarchical system that's distributed globally across a conglomeration of DNS servers. The service acts as a giant directory for resolving domain names to IP addresses and IP addresses to domain names, irrespective of where the domains are located.
The DNS system allows internet users to access content by remembering a name rather than an IP address. For example, DNS makes it possible for users to type techtarget.com in a browser to connect to the TechTarget website, without knowing the associated IP address.
Internet domains are identified by unique IP addresses. These addresses make it possible for a device connected to the internet to communicate directly with a specific domain. DNS simplifies communications using a hierarchical naming structure.
At the top of this hierarchy is the Root domain, which serves as the parent node for all internet domains. The root domain contains multiple top-level domains (TLDs) that sit directly beneath it in the DNS hierarchy. TLDs identify geographic or purpose commonality, such as a nation or commercial enterprise. For example, TLDs include .com, .net, .org, .gov and several other domains, including country codes.
Individual domains -- such as techtarget.com, usda.gov or redcross.org -- sit directly beneath the TLDs. Each second-level domain is associated with a specific TLD, as indicated by the final component of the domain name. For example, techtarget.com is located within the .com TLD, usda.gov is part of the .gov TLD, and redcross.org is within the .org TLD. A second-tier domain can also include subdomains, as in searchstorage.techtarget.com or searchdatabackup.techtarget.com, which are part of the second level techtarget.com domain.
What is a network domain?
The term domain is also used in other types of networks to describe the logical organization of connected physical network resources and users. This type of domain provides a structure for managing network resources and users under a single administrative umbrella. A network domain typically includes servers, desktops, printers and other devices. It also provides a mechanism for authorizing and authenticating users for network access. Administrators can control which resources a user can access and the user's level of access.
A network domain makes it possible to organize network resources and users based on the needs of the organization and the types of resources connected to the network. Administrators can apply policies to network resources at a granular level. A user logs in to the domain to access the approved resources, regardless of where the resources are located on the network. The domain also enables users on the network to communicate and collaborate.
A domain can include resources and users on a local area network (LAN) and wide area network (WAN). The platform that manages the domain, such as Active Directory Domain Services (AD DS), commonly includes features to help client computers locate the nearest resources and optimize processes such as replicating directory data between distributed servers.
A common network domain used today is Active Directory designed by Microsoft for Windows domain networks. Active Directory stores information about objects and users on the network and provides a logical, hierarchical view of the directory information, making it easy for administrators and users to navigate the domain and find resources. It also offers integrated security, including login authentication and access control to directory objects.
The Active Directory domain typically includes one or more domain controllers for managing resources and users across the network. A domain controller is a server that does the domain's heavy lifting. It maintains details about network resources, stores user account information and processes authentication requests for access to network resources. It also handles operations such as replicating directory data with other domain controllers. Although domain controllers are mostly used in Active Directory domains, they are also used in some non-Windows environments.
What is domain knowledge?
The term "domain knowledge" is used to describe a sphere of knowledge in a specific field or industry. Commonly used in the technology industry, this term refers to an individual's capabilities beyond his or her basic skill set. For example, someone applying for a project management position on a development team might be expected to have domain knowledge about DevOps development methodologies, tools and environments.
Domain knowledge in this sense is a subjective concept whose meaning depends more on circumstances than a dictionary definition. For example, a software engineer's domain knowledge might refer to knowledge about an application's operating environment or about the way end users interact with the application.
See also: networking, World Wide Web, domain generation algorithm
