endpoint device
What is an endpoint device?
An endpoint device is an internet-capable computer hardware device on a TCP/IP network. The term refers to desktop computers, laptops, smartphones, tablets, thin clients, printers and other specialized hardware, such as actuators, point of sale (POS) terminals and smart meters.
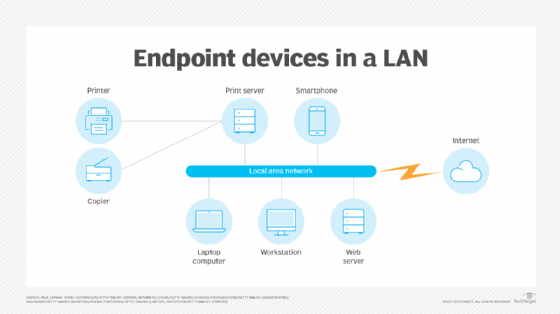
In an office setting, various devices are endpoints connected to the internal local area network (LAN). The LAN, in turn, is connected to the internet.
Why are endpoints important?
Endpoint devices are often end-user devices that provide the user interface to computer networks, the internet and its many resources, and any kind of information system. None of the activities that users worldwide perform daily would be possible without endpoints.
Endpoints also provide other services, depending on their function. For example, sensors capture performance data on specialized systems, such as those that monitor radiation levels in a nuclear power station.
Examples of endpoint devices
Some of the common endpoint devices include the following:
- Desktop computers. People working in offices often use these endpoint devices. Desktops provide the primary interface for users to perform tasks such as document editing, web browsing and accessing network resources.
- Laptops. These portable endpoint devices let users work from anywhere. They provide similar functionality to desktop computers, but have the added benefit of portability. They enable users to access the network and perform tasks on the go and from remote locations.
- Smartphones. These mobile devices connect to a computer network via a cellular network or Wi-Fi. They provide a range of functionality, including communication capabilities for calls, texts and emails; web browsing; and access to applications. They also can be used as a mobile hotspot to provide internet connectivity to other devices.
- Tablets. These lightweight, portable devices offer a larger screen than smartphones, but are smaller than laptops. They're commonly used for web browsing, email, multimedia consumption and accessing cloud-based applications.
- Printers. These peripheral devices connect to a computer network and can be accessed by multiple users to print documents, photos or other forms of visual media.
- POS systems. These systems are used in retail and other commercial environments for sales transactions. They typically include a combination of hardware, such as a touchscreen display, barcode scanner, cash drawer and receipt printer, along with software for sales processing, inventory management and other business operations.
- Internet of things (IoT). IoT devices are a diverse range of network-connected devices that extend beyond traditional computing devices. Examples include smart home devices, industrial sensors, wearable devices and connected appliances. They typically collect and transmit data to the network, and perform specific tasks based on that data, such as adjusting temperature settings or monitoring equipment.
Who uses endpoint devices?
Virtually everyone is an endpoint user. Anytime someone uses a device that connects to a LAN or the internet, they are using an endpoint device. Networking elements, such as routers, switches and gateways, can also be considered endpoints because they connect to network resources and endpoints alike.
Despite advances in endpoint device development, they still represent an important attack surface for cybercriminals and other threat actors. Endpoints shouldn't be deployed without sufficient cybersecurity measures.
Endpoint management
Management of endpoint devices is important as part of an overall device management strategy. Some ways that endpoint device management comes into play include the following:
- Bring your own device (BYOD) policies. Organizations that permit employees to use their own computing devices under a BYOD policy must be able to keep track of such devices and ensure they don't provide an access point for malware and other cyberthreats.
- Company-provided devices. Employees are often required to use company-provided computers that have been configured with security policies and programming to minimize the attack surface. Remote work situations have employees using virtual private networks and other systems to access company resources. These are also managed by applications installed on the company devices.
- Location and status. Tracking the location and status of user devices is an important part of device management.
- Inventories. Device management also maintains the inventory of devices in use, units being repaired and refurbished, and devices slated for disposal or replacement.
Establishing endpoint policies
Endpoint protection platforms and policies for endpoint device management are essential parts of security and business strategy. They specify how endpoints are used and configured, access controls, installed security components, and other metrics.
Experts recommend a policy-based approach to network security that requires endpoint devices comply with specific criteria before they're granted access to network resources. Security parameters are defined in the endpoint policy, such as a zero-trust approach for network access.
A BYOD policy is also advised to specify the circumstances under which a noncompany device can be used on the company network. The policy should include guidance on remote access and the configuring and disabling of endpoints.
To automate the process, software that handles endpoint device management is available from cloud service providers as well as with on-premises systems. In addition to inventory management, systems such as Microsoft Intune can configure new devices for use on company networks, monitor BYOD equipment to ensure the company's security policies are being followed and push updates out to each device.
The importance of endpoint security
Endpoints are pathways for potential security vulnerabilities and data breaches. Security measures must be taken to protect systems from data loss and other types of attacks. Those measures include access controls to prevent unauthorized access to information resources, such as two-factor authentication and multifactor authentication to validate a requesting user.
Security tools such as antivirus and anti-ransomware software can be built into an endpoint device. Endpoints without local access security, such as a thin client, will need to perform access authentication with the system to which the endpoint connects to reduce security risks. These controls are in addition to network protection components, such as firewalls and intrusion prevention systems.
Endpoint protection involves everything from asset discovery to device profiling. Learn more about endpoint security best practices and how it enhances data security.
