image
What is an image?
An image is a visual representation of something, while a digital image is a binary representation of visual data. These images can take the form of photographs, graphics and individual video frames. For this purpose, an image is a picture that was created or copied and stored in electronic form.
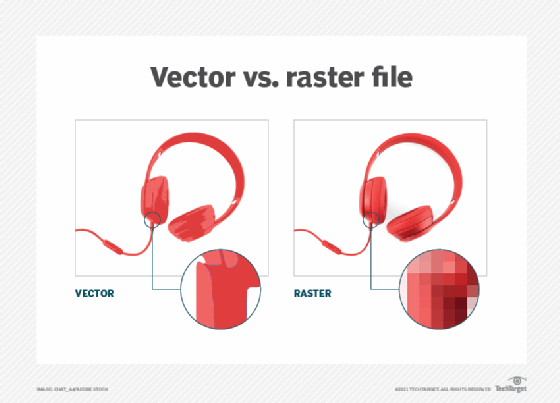
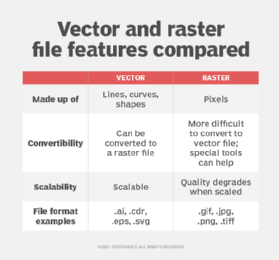
An image can also be described in terms of vector graphics or raster graphics. An image stored in raster form is sometimes called a bitmap. An image map is a file containing information that associates different locations on a specified image with hypertext links.
Standard digital image file formats include the following.
JPEG
JPEG (pronounced JAY-peg) is a graphic image file produced according to the Joint Photographic Experts Group standard. This group of experts develop and maintain standards for a suite of compression algorithms for computer image files. JPEGs usually have a .jpg file extension.
GIF
GIF (pronounced JIF by many, including its designer, and pronounced GIF with a hard G by others) stands for Graphics Interchange Format. GIFs use a two-dimensional (2D) raster data type and are binarily encoded. GIF files usually have the .gif extension.
GIF89a is an animated GIF image format. The primary benefit of this format is the ability to create and play an animated image on a webpage. A twirling icon, a banner with a hand that waves or letters that magically get larger are examples of animated GIFs. GIF89a can also be specified for interlaced GIF presentations.
PNG
PNG (pronounced ping) is the Portable Network Graphics file format for image compression. It provides several improvements over the GIF format. Like a GIF, a PNG file is compressed in a lossless manner, meaning that all image information can be restored when decompressing the file for viewing. PNG files typically have a .png extension.
SVG
SVG (Scalable Vector Graphics) is a vector file used to display 2D graphics, charts and illustrations online. SVG files do not depend on unique pixels to create images so they can scale up or down without losing resolution. This means that the file can be viewed on a computer display of any size and resolution, such as the small screen of a smartphone or a large widescreen display on a PC.
SVG files are also searchable and indexable since they use an Extensible Markup Language (XML) format. Any program, such as a browser, that recognizes XML can display the image using the information provided in the SVG file. SVG files usually have an .svg extension.
TIFF
TIFF (Tag Image File Format) is a standard format for exchanging raster graphic (bitmap) images between application programs, including those used for scanner images. TIFF files have a .tiff or .tif file name suffix.
What is a disk image?
A copy of the entire contents of a storage device, like a hard drive, is called a disk image. Disk images represent the content exactly as it was on the original storage device, including data and structure information.
A section of RAM copied to another memory or storage location is also known as an image.
What is image stabilization?
In photography and videography, image stabilization is a technique or process used to stabilize images and videos that occurs when the camera shakes because of unsteady hands.
What is image resolution?
The details held by a particular image are known as image resolution. The higher the resolution, the more visible the details are in an image. Image resolution quantifies how close lines can get to each other while remaining visibly resolved. Resolution units are tied to physical dimensions, angular subtense or the size of a picture (television lines, or TVL).
What is image processing?
Image processing describes the process of digitally transforming an image and executing specific operations to obtain useful information from it. Image processing systems often treat images as 2D signals when applying some predetermined signal processing approaches.
Types of image processing include the following:
- pattern recognition to measure various patterns around objects in an image;
- recognition to detect or differentiate objects within an image;
- retrieval to browse or search an extensive image database for an image like the original image;
- sharpening and restoration to create an enhanced image from the original image; and
- visualization to identify objects not visible in an image.
What is image segmentation?
The division of an image into categories or regions that correspond to various objects or parts of an object is called image segmentation. Each pixel in an image is allocated to one of these categories. Dividing and segmenting visual inputs make image analysis more straightforward. Each segment is composed of sets of one or more pixels. Image segmentation involves sorting pixels into larger components without having to consider each pixel as a unit.
What is image retention?
A temporary or permanent residual image on a screen is known as image retention. Image retention sometimes occurs on screens when an image is displayed for an extensive period. This occurs because of the different characteristics of the materials used to achieve high-definition imaging. It is best to avoid images susceptible to image retention to protect digital screens whenever possible.
What is digital image correlation?
Digital image correlation (DIC) describes the surface displacement measurement technique of capturing a solid object's motion, shape and deformation. It is difficult to achieve reliable and high-quality DIC results but easy to obtain rudimentary DIC results.
Also, see imaging and image metadata.
