infinite loop (endless loop)
What is an infinite loop?
An infinite loop -- sometimes called an endless loop -- is a piece of code that lacks a functional exit so that it repeats indefinitely. In computer programming, a loop is a sequence of instructions that is continually repeated until a certain condition is reached.
Infinite loops can be used intentionally or can occur as the result of a programming error or a bug. A pseudo-infinite loop is one that looks as if it will be infinite but stops at some point.
The term infinite loop is sometimes used to describe an endless iteration situation in DevOps feedback loops and software development processes.
What is a loop in programming?
A loop in computer programming is created when a sequence of instructions repeats until a certain terminating condition is reached. Typically, a defined process is completed -- such as getting an item of data and changing it -- and then a condition is checked, such as whether a counter has reached a prescribed number. Once the prescribed number is reached the loop ends.
Loops are used to execute the same code multiple times. For example, code that checks the attendance status of each student in a classroom could return a Y for present and an N for absent. The program would need to run through the class roster of 26 students and do this for each member of the class. The program's stopping condition would occur after 26 students had been checked.
There are different types of loops, and different programming languages have different loop syntaxes. Some types of loops include the following:
- A for loop repeats a block of code a known number of times. It iterates through a list and runs code once for each item in the list.
- A while loop will continue to repeat as long as a specified condition is met. It checks for the condition before running the loop code.
- A do loop runs code, then checks for the condition afterward.
- A do-while loop is like a while loop but puts the condition at the end, so that the loop runs at least one time if the condition is not met. A while loop will not run if the condition is not met.
No matter the loop type or language syntax, most loops have an exit condition that tells the loop when to end.
How do infinite loops work?
Infinite loops continue as long as the exit condition doesn't occur. A loop without an exit condition happens when one of the following conditions exists:
- The loop has no terminating condition.
- The loop has a terminating condition that cannot be met.
- The loop has a condition that instructs it to start over.
In the attendance checking program example, the 26 students are listed in alphabetical order and labeled numerically, with the first student on the list being number one and the last student being number 26. In this case, the loop would normally be set to terminate after the loop runs 26 times. However, the following criteria could turn it into an infinite loop:
- No terminating condition is set, and the loop returns to student one and checks through the entire list over and over again.
- The terminating condition is set to a number that does not fall into the list of 26 students, such as -1 or 316.
- The loop contains instructions to return to student one sometime before 26 is reached or a break statement is written that causes an intentional interruption in the loop.
In all cases, if the presence of the specified condition cannot be ascertained, the next instruction in the sequence tells the program to return to the first instruction and repeat the sequence. This typically continues until the program terminates automatically after a certain amount of time, or the operating system (OS) terminates the program with an error.
Why are infinite loops used?
An infinite loop often results from a programming error. For example, the conditions for exit are incorrectly written.
However, there are instances when an infinite loop is used intentionally, enabling a program to run continuously. Some examples include the following:
- Embedded systems. A cartridge-based video game is an embedded system that uses an infinite loop. The game runs an infinite loop until the console is powered off because there is no underlying OS to return to.
- Operating systems. OSes are infinite loops that continually check for user input and respond accordingly. The loop continues until the device is turned off or reset.
- Web servers. Web servers are designed to take a request, return a webpage and then wait indefinitely for the next request.
- Viruses. Malware can use infinite loops to overwhelm a computer's processing power and cause it to crash. This technique is used to carry out a distributed denial-of-service attack, which occupies a computer or network's resources so that legitimate users can't access them.
The following joke captures the spirit of infinite loops such as malware:
- Q: Why did the programmer die in the shower?
- A: Because the bottle said "lather, rinse, repeat."
The programmer, thinking like a computer, presumably lathered and rinsed repeatedly until they died of exhaustion, starvation or drowned.
Infinite loop examples
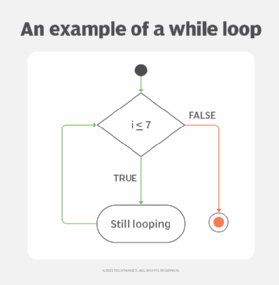
The following is an example of infinite loop code in Python:
i=1
while i <= 7
print ("still looping")
In this loop, the program checks the value of i, then says that if i is less than or equal to 7, the program will print the phrase "still looping." The exit condition is if i is greater than 7. Since there is nothing changing the value of i, this exit condition cannot be fulfilled. The program will print the phrase "still looping" indefinitely until the computer is shut off or crashes.
Infinite loops can appear in a variety of computing contexts and are used in a variety of programming languages. In some contexts, loop conditions can cause a cybersecurity breach. Cybersecurity professionals should learn these 5 essential programming languages to be able to stop these threats and others effectively.
