computer instruction
What is a computer instruction?
A computer instruction is an order given to a computer processor by a computer program. At the lowest level, each instruction is a sequence of 0s and 1s that describes a physical operation the computer is to perform.
Computer instructions typically have three fields. These include an operation code, or opcode, field that identifies the operation to be performed, such as "add" data in memory to a specific register. They also have an address field, showing where registers and memory are located, and a mode field, showing how the registers and memory will perform.
Instructions vary in length. They can be a few bits long or many bytes. A very long instruction word (VLIW) is a processing architecture where the instructions are processed in parallel. VLIW is mostly used in high-performance, embedded applications. Reduced instruction set computer, or RISC, microprocessors are designed to perform a small number of computer instruction types, often of fixed lengths.
How do computer instructions work?
Computer programmers provide the instructions that the computer system needs, using a keyboard or other type of input device. The computer's operating system (OS) or other software applications are programmed to interpret and execute these instructions.
Depending on the particular instruction type, instructions specify special storage areas called registers that may contain data to be used in carrying out an instruction. Instructions also specify the location in computer memory of the data and the input/output (I/O) format to be used.
In a computer's assembler language, each language statement generally corresponds to a single processor instruction. In high-level languages, such as C++, a language statement generally results after the program is compiled in multiple processor instructions.
In assembler language, a macro instruction is one that expands to become multiple instructions during the assembler program processing. The exact way this works is based on a previously coded macro definition.
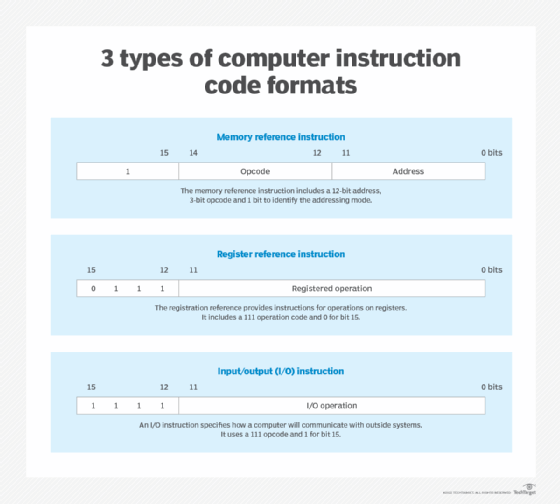
How instruction sets work
A collection of computer instructions is an instruction set. It facilitates a variety of tasks for a computer system's central processing unit (CPU) to execute. A basic computer has a computer architecture designed to link all components together into a cohesive system. The computer organization generally includes a CPU, memory, I/O components, firmware that contains the OS and specific control instructions on how the computer functions.
The following are the principal categories of instructions a computer must have to process information:
- computing capabilities, including arithmetic, shift and logic instructions;
- instructions that move information into and out of registers that are associated with the CPU and memory;
- program control instructions that also check the status of program activity; and
- instructions for I/O activities.
A considerable amount of information is stored in memory registers, but all computational and general processing activities occur in CPU registers. Branching instructions handle changes in how a program executes. I/O instructions move data into memory for subsequent processing regimes and then deliver the results to the user.
The 3 components of computer instructions
The computer instructions that programmers provide are made up of three fields. These fields are the following:
- Opcode field. This field describes the operation that is to be performed.
- Address field. This field indicates where register or memory addresses are located. These are referred to as the operands or the data that will be operated on or manipulated.
- Mode field. This field specifies how the operand will perform.
Quantum computers loom as one of the next big steps in computing. Find out what you need to know about quantum computer programming.
