instruction set
What is an instruction set?
An instruction set is a group of commands for a central processing unit (CPU) in machine language. The term can refer to all possible instructions for a CPU or a subset of instructions to enhance its performance in certain situations.
All CPUs have instruction sets that enable commands directing the CPU to switch the relevant transistors. The instructions tell the CPU to perform tasks. Some instructions are simple read, write and move commands that direct data to different hardware elements.
The instructions are made up of a specific number of bits. For instance, The CPU's instructions might be 8 bits, where the first 4 bits make up the operation code that tells the computer what to do. The next 4 bits are the operand, which tells the computer the data that should be used.
The length of an instruction set can vary from as few as 4 bits to many hundreds. Different instructions in some instruction set architectures (ISAs) have different lengths. Other ISAs have fixed-length instructions.
What are some types of instruction sets?
The various types of instruction sets include the following:
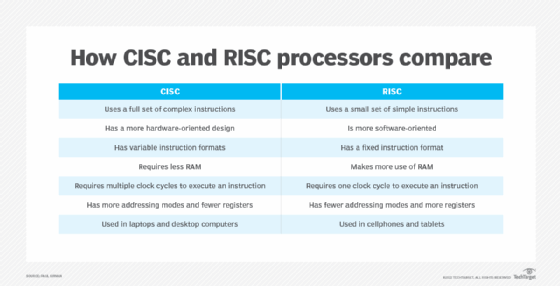
- Complex instruction set computer. CISC processors have an additional microcode or microprogramming layer where instructions act as small programs. Programmable instructions are stored in fast memory and can be updated. More instructions are included in CISC instruction sets than in other types of instruction sets. A single instruction can initiate multiple actions by the computer, such as a single add command launching multiple memory access load and store instructions.
- Reduced instruction set computer. RISC architecture has hard-wired control. It does not require microcode, but has a greater base instruction set. RISC also uses a smaller and more compact instruction set with a fixed instruction format. RISC processors are designed to process faster and more efficiently.
- Enhancement instruction sets. These instruction types are more familiar because they are often used in marketing CPUs. Examples of this go back to the 166-megahertz Intel Pentium with MultiMedia Extensions (MMX) technologies. It was introduced in 1996 and marketed with enhanced Intel CPU multimedia performance. MMX refers to the extended instruction set.
Why are instruction sets important
The ISA is fundamental for building fast, efficient computers that optimize memory and processing resources. It specifies the following supported capabilities:
- instructions
- data types
- processor registers
- main memory hardware
- input/output model
- addressing modes
Programmers and system engineers rely on the ISA for guidance on how to program various activities.
Instruction sets work with other important parts of a computer, such as compilers and interpreters. Those components translate high-level programming code into machine code that the processor can understand.
Think of the ISA as a programmer's gateway into the inner workings of a computer. It is essential when working with application development, assembly language and compilers. It sets the rules for the hardware and software interface, defines what the CPU does and ensures compatibility.
How are instruction set commands used?
The following are three main ways instruction set commands are used:
- Data handling and memory management. Instruction set commands are used when setting a register to a specific value, copying data from memory to a register or vice versa, and reading and writing data.
- Arithmetic and logic operations and activities. These commands include add, subtract, multiply, divide and compare, which examines values in two registers to see if one is greater or less than the other.
- Control flow activities. One example is branch, which instructs the system to go to another location and execute commands there. Another is jump, which moves to a specific memory location or address.
