intranet
What is an intranet?
An intranet is a private network contained within an enterprise that is used to securely share company information and computing resources among employees. An intranet can also be used for working in groups and teleconferences.
Intranets encourage communication within an organization. They let employees easily access important information, links, applications, forms and databases of company records. A database that includes all the usernames of employees who have access rights to the network is often used to maintain intranet security.
How are intranets used?
Organizations use intranets in a variety of ways depending on their needs. These include the following:
- Central repository. Intranets become the main repository where important information and company data are stored.
- Collaboration. These internal networks provide a way to share information that makes it easier for employees to work together.
- Personalization. Intranets provide personalized content to employees based on their role within the company.
- Communication. They make employee directories, company news and organization charts readily available, improving internal corporate communications.
- Easy access to information. Intranets provide easy access to information about company policies, benefits and updates.
- Social elements. Social media features let employees create an account, post content and status alerts and browse a newsfeed.
- Project management. To-do lists, employee directories, status updates and other resources aid users in project management.
- Automation. Intranets streamline everyday activities by helping to automate repeatable tasks.
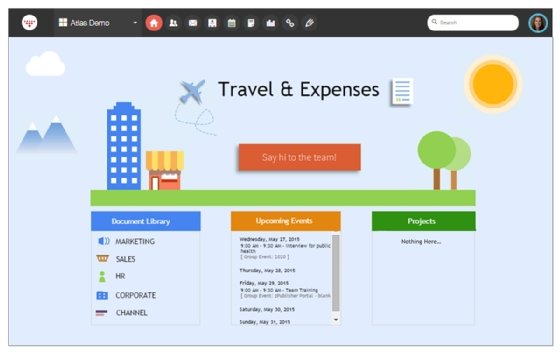
How do intranets work?
A secure and reliable intranet requires a web server that manages requests for data hosted on the server. The web server finds requested files and delivers them to the appropriate user. A content management system should also be set up to control the creation, publication and management of intranet content.
An intranet may also consist of many interlinked local area networks (LANs), as well as leased lines connecting to wide area network resources. The intranet's web server uses TCP/IP, HTTP and other internet protocols. Typically, an intranet includes connections through one or more gateway computers to the outside internet and external resources.
To access their company intranet, employees must have a special network password and be connected to the company LAN. Remote employees access the intranet through a virtual private network (VPN) or another secure connection. The VPN lets users not actually connected to the required LAN sign into the intranet and access all the same information and functions that would be available had they been connected to the LAN.
Firewall software is essential to the security of an organization's intranet. It stands between the outside internet and the private intranet. The firewall will track all incoming and outgoing data packets to confirm they do not contain unauthorized or suspicious requests. Firewalls also ensure malware and other malicious attacks do not penetrate the intranet.
When a segment of an intranet is made accessible to customers, partners, suppliers or others outside the company, that segment becomes part of an extranet. A firewall is especially important to secure intranet networks that include extranet extensions.
The intranet generally looks like a private version of the internet. With tunneling, companies can send private messages through the public network. They use special encryption and decryption and other security safeguards to connect one part of their intranet to another.
Hosted software applications also provide intranets. Instead of a company having its own private server, it buys intranet software that performs the same functions as traditional intranets. Some modern intranets operate similarly to social media applications that connect to an array of corporate applications. These applications are also called employee experience platforms.
What are the advantages of an intranet?
Some potential benefits of using an intranet include the following:
- improved communication, information sharing and collaboration within a business;
- simplified records management;
- streamlined tracking of requests;
- a testing environment for new ideas before they are implemented on a company's webpage;
- improved corporate culture that focuses on employees and encourages participation and interaction; and
- a favorable return on investment from low implementation and operating costs.
What are the disadvantages of an intranet?
There are also challenges when implementing an intranet, including these:
- Low user participation rates can result in a lack of the content, communications and documents needed to make the intranet beneficial.
- The high cost of personnel leads to inadequate support for intranet users. As a result, when software bugs or other issues arise, problems are not resolvedquickly.
- The network must be managed, with regular inspections and maintenance checks to ensure it is running properly and content is fresh and relevant.
- A lack of proper ownership or ownership being distributed among groups complicates network responsibilities and management.
- A lack of mobile device and remote support creates problems, including limiting the ability of remote workers to access information on the intranet.
How do intranets, the internet and extranets differ?
The internet, intranets and extranets are different types of networks with some similarities and overlapping aspects.
Internet
The internet works on a public network that anyone can access. There are no limits on who can access the internet, other than users must have access to a computing device that's connected to the internet. The public internet can have unlimited users at any one time, but it is more vulnerable to attackers than an intranet.
Intranet
An intranet works on a private network of computers. Only authorized people and systems can access it. They also must connect to the intranet via the required LAN or VPN. An intranet typically can host a specific number of users.
Extranet
An extranet is an intranet that grants access to those outside of an organization to certain information and applications. Third parties such as customers, vendors and partners are given access to certain parts of the organization's intranet.
What are intranet best practices?
Intranets were developed around the same time as the internet and evolved alongside it. Some best practices for an intranet strategy in the modern Digital workplace include the following:
Multichannel approach. A modern intranet should incorporate other team collaboration tools inside the main intranet application. It should centralize disparate applications, which may include collaboration and communication tools, tools for virtual conferences and line-of-business applications.
Optimize for remote work. Many older intranet platforms were not optimized for mobile or remote workers. Intranet applications should be easy to access without the use of a corporate desktop or laptop PC. Intranets should let remote workers access resources without having to be online constantly.
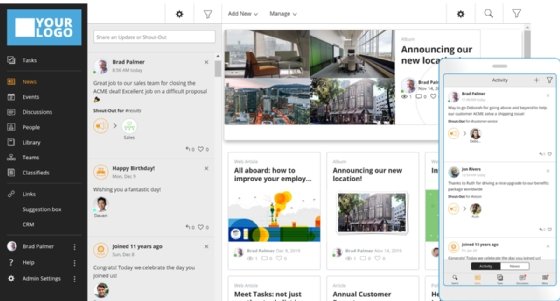
Modern user experience. To ensure user participation, intranet platforms should be engaging. They often resemble consumer applications that put a focus on ease-of-use and the user experience. A smart homepage that users can customize is a plus.
Regular engagement. Regularly posting fresh content boosts user engagement and fosters a sense of community. Intranets can be used to create smaller groups within a company based on employee interest. They can also be used to enable peer-to-peer acknowledgment of jobs well done. Making the corporate intranet a place where employees are encouraged to communicate with one another strengthens company culture and provides insight into employee needs.
What are examples of intranets?
Intranet platforms are available from large vendors and smaller startups. They include the following:
- Axero
- Blink
- Facebook Workplace
- Happeo
- HCL Connections
- HyperOffice Atlas
- Jostle
- Microsoft SharePoint
- Microsoft Yammer
- Passageways OnSemble
- Samepage
- Simpplr
- Staffbase
- Workvivo
- Zoho Connect
What's next for employee engagement?
The intranet is being rethought as companies look more broadly at their employee experience strategies. Employee experience applications are replacing many functions of intranets. These applications take into account the distributed nature of work, the need to enable greater flexibility and the various enterprise applications and resources that must be centralized.
Learn about seven types of employee experience applications that provide the tools organizations need to collaborate.
