
lift and shift
What is lift and shift?
Lift and shift is a strategy for moving an application or operation from one environment to another without stopping to redesign the app's or operation's workflow. The complexity of an application or operation is a key factor in deciding whether something should be lifted and shifted or re-architected from scratch as a new native cloud app or operation.
Lift and shift is also known as re-hosting. It's most often used to move an app and its associated data from an on-premises data center to the public cloud.
In the early days of cloud computing, the lift-and-shift approach was often used to replicate on-premises apps in the cloud, while avoiding costly, time-consuming redesign. However, many legacy colocation applications that were lifted and shifted to the cloud weren't able to take full advantage of the cost efficiencies of native cloud features, including autoscaling. While commercial, off-the-shelf applications with easily defined patterns were good candidates for lifting and shifting, re-architecting was a better option for resource-intensive apps, such as those used for big data analytics and image rendering.
Forrester researchers predicted that 2022 and beyond would see organizations move away from the lift-and-shift approach.
Benefits of lift and shift
The lift-and-shift cloud migration strategy offers the following advantages for businesses looking to move their applications to the cloud:
- Speed. Lift-and-shift migration is often the fastest way to migrate applications to the cloud. By minimizing the need for redesign or modification, businesses can quickly transfer their existing applications and workloads to the cloud platform.
- Simplicity. This migration method often requires minimal changes to the existing application, making it straightforward and efficient. Lift and shift lets businesses focus on other aspects of their digital transformation, while ensuring a smooth transition to the cloud.
- Cost savings. Lift and shift is considered a less expensive upfront option for cloud migration. This enables companies to optimize their spending on IT infrastructure and reduce overall costs.
- Minimal business disruption. Lift and shift doesn't involve substantial changes, enabling organizations to maintain functionality and user experience during migration.
Disadvantages of a lift-and-shift approach
There are some disadvantages to a lift-and-shift approach when compared to application re-factoring, also known as re-architecting. While it's usually best to re-factor an application as part of a migration, sometimes, organizations need to do so retroactively.
This article is part of
What is cloud migration? Essential guide to moving to the cloud
Lifting and shifting is often compared to moving a houseplant from one environment to another -- being in a different habitat can affect whether the plant thrives. Likewise, an IT project that started in an on-premises or original legacy system might not work as well in a new location.
For example, a lift-and-shift project that starts without sufficient documentation of requirements or operational design can easily go awry. The unfortunate results often involve data that is mismatched to its handling systems or data sets that outgrow their environment. Resource-intensive apps may need to be redesigned from scratch as cloud-native apps to avoid performance and latency issues.
Re-factoring may also be necessary when performance fails to meet expectations after a lift and shift, especially when tuning doesn't solve the problem. An application that's been moved to the cloud might benefit from re-factoring when costs spike due to application or database inefficiencies. This is also true when security vulnerabilities arise because the application can't integrate with native security systems, such as identity and access management tools.
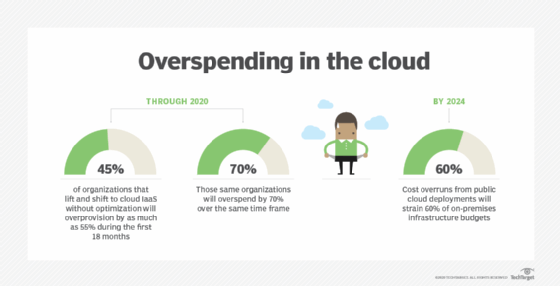
Lift and shift vs. refactoring
There are various approaches to cloud migration. A common approach is to lift and shift an application to the cloud to reduce on-premises IT infrastructure costs in the short term but then to re-factor the app once it's in the cloud. Re-factoring involves modifying components of an application, such as structure, design and code.
Lift and shift and re-factoring are also used separately. While lift and shift migrates applications to the cloud with minimal changes, re-factoring involves re-architecting applications to take full advantage of the cloud environment. This may involve modifying the application's code or architecture, making it more suitable for the cloud infrastructure and enabling it to use native cloud features.
Lift and shift is cost-effective and requires little upfront effort in the migration process. Re-factoring, on the other hand, can offer long-term benefits, such as better performance and increased stability. However, these benefits require more upfront time and resources than lift and shift.
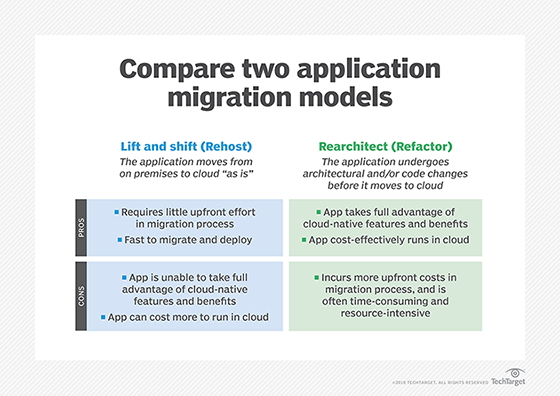
Lift and shift vs. SaaS
Software as a service (SaaS) is another option for businesses looking to move their applications to the cloud. SaaS offerings are third-party applications that a cloud provider hosts and maintains. Businesses access and use the software without the need for in-house infrastructure or maintenance.
While lift and shift focuses on migrating existing applications to the cloud, SaaS involves adopting ready-made cloud-based applications that replace the need for on-premises applications. SaaS applications offer several advantages, including reduced costs, faster implementation and simplified management.
However, SaaS may not be suitable for every business or application. Some organizations require more control over their applications or have specific customization needs that SaaS apps can't accommodate. In such cases, lift and shift or re-factoring may be more appropriate migration strategies.
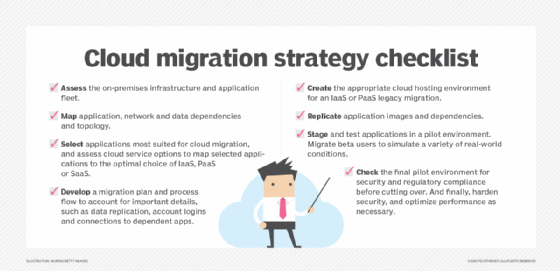
Top uses of lift and shift
The lift-and-shift strategy is best suited for specific situations, including the following:
- Third-party applications that can't be re-factored or modified, only lifted and shifted.
- Legacy applications that are difficult to re-factor or re-platform because of their age or complexity.
- Businesses operating under a time constraint that need to migrate their applications fast and cheaply.
- Hybrid cloud deployments in which an organization needs to maintain its existing on-premises infrastructure for certain workloads, while using the cloud for others.
Lift-and-shift preparation
Before undertaking a lift-and-shift migration, businesses should consider the following steps to ensure a successful transition:
- Assess applications. The existing applications should be examined to determine if they're suitable for lift-and-shift migration or whether they require re-factoring or replacement with SaaS applications.
- Develop a migration plan. A comprehensive cloud migration strategy should be developed outlining the steps and resources required for the migration process, including timelines, responsibilities and contingencies.
- Ensure security. The applications should be reviewed for security vulnerabilities and measures taken to protect data and systems during and after migration. Ignoring the importance of security can be a mistake for any cloud migration strategy.
- Select a cloud provider. A cloud provider should be chosen that offers the cloud services and support necessary for the specific applications and workloads.
- Monitor and optimize. After the migration, the applications and cloud infrastructure should be continuously monitored to identify areas for optimization, cost savings and performance improvements.
Lift and shift is just one approach to cloud migration. Learn the 12 key steps for a successful cloud migration.