managed detection and response (MDR)
What is managed detection and response (MDR)?
Managed detection and response (MDR) services are a collection of network-, host- and endpoint-based cybersecurity technologies that a third-party provider manages for a client organization. The provider typically installs technology on-premises at the client organization and provides additional external and automated threat hunting services.
MDRs improve cybersecurity by searching for threats and responding to them once detected. They also let users connect with the provider's security experts, who can bolster the security skills of the client company's IT department. This makes them ideal for businesses that don't have a designated in-house threat detection team.
Managed detection and response services are growing in popularity partially because of the growing skills gap in cybersecurity. Gartner predicts that by 2025, 50% of all enterprises will have adopted MDR services.
Benefits of MDR
MDR services play an active role in improving a business's information security strategy. They handle threat detection, incident response, continuous monitoring and IT asset analysis.
MDR services approach these tasks in a way that mitigates common problems modern IT departments usually face. They provide the following benefits:
- Management of high alert volume. MDRs can help companies manage the sheer volume of cybersecurity alerts that must be checked on an individual basis. Too many false alerts can cause alert fatigue in smaller security teams, making them neglect other responsibilities.
- Threat analysis. Many alerts do not immediately present themselves as a threat and require thorough analysis to determine their status. MDR services provide advanced analytics tools, threat intelligence and access to security experts to help with this, interpreting events and providing recommendations for improvement.
- Access to security expertise. In a Cybersecurity Workforce study conducted by ISC2, 67% of participants stated that their company lacks the cybersecurity personnel necessary to detect and resolve security problems. Furthermore, 92% of respondents state that their company has a skills gap, with cloud computing security, artificial intelligence, machine learning and zero-trust adoption being the most prevalent. MDR services can mitigate this by providing access to their team of experts, who usually work 24/7 to monitor a network and are available for consultation.
- Endpoint detection and response (EDR). Businesses may lack the funds, time, or skills to train employees for EDR tools. MDR services come with EDR tools and integrate them into detection, analysis and response processes, eliminating the need for extensive in-house endpoint security.
- Around-the-clock monitoring. MDR vendors guarantee constant surveillance and threat detection by providing customer networks with nonstop protection and monitoring.
- Proactive threat hunting. An organization's security stack can't always detect every security event. However, most MDR providers proactively scan the network and systems of a company for signs of an active attack and take swift mitigation actions.
- Rapid incident response. MDR services offer rapid response times to advanced threats and security incidents. Security teams can swiftly detect unusual activities, consistently identify cyberthreats and take prompt action to mitigate them.
- Cloud threat monitoring. MDR services commonly involve the monitoring and protection of cloud environments. This is especially valuable for organizations relying on cloud infrastructure, ensuring thorough cloud security coverage across multiple platforms.
- Customized security rules and services. MDR services generally offer organizations the ability to personalize security rules according to their unique needs. This adaptability enables customized threat detection and response strategies.
What are the challenges of MDR?
As with many anything-as-a-service models that outsource modern IT processes, corporations trade some control for more convenience and more flexible prices. MDR services do have some downsides when compared to older managed security products and depending on the client's intended use for the services.
Common challenges that come with MDR services include the following:
- Complex deployment. Deploying MDR can sometimes be difficult, especially for enterprises with varying IT environments. Integrating MDR tools and technologies into current systems and processes also involves rigorous planning and coordination.
- Cost considerations. MDR services might pose a financial challenge, especially for small and medium-sized organizations operating within tight budgets. Therefore, it's crucial to thoroughly evaluate and justify the costs associated with outsourcing MDR services.
- Integration with existing infrastructure. To ensure the effectiveness of MDR services, an organization's current security posture -- network monitoring tools, endpoint protection programs, and security information and event management systems -- should seamlessly integrate with them. However, ensuring consistent compatibility and integration can be challenging.
- Evolving threat landscape. The threat landscape evolves constantly, with new cyberattacks and malware variants emerging regularly. MDR service providers must remain abreast of the latest cybersecurity threats as well as consistently update their detection and response capabilities to counter them effectively.
- Inadequate responses. Not all MDR agencies are created equal. While some are meticulous in finding and managing threats, others might not be so vigilant. For example, some agencies might only trigger generic alerts -- "There is a critical alert on your firewall, and you should investigate further" -- after a security event. The businesses using those services must do more troubleshooting and remediation on their own.
MDR vs. classic managed security
Both MDR and classic managed security products perform the same general function: externally assisting companies with cybersecurity. However, there are a few core differences between MDR services and classic managed security services:
- Compliance. Classic managed security services -- sometimes called managed security service providers (MSSPs) -- are typically focused much more on compliance reporting and helping businesses meet compliance requirements. MDR services rarely focus on this.
- Log format. MSSPs are generally able to work with a wider variety of event logs and contexts. MDRs primarily just use the logs that come with their tools.
- Human interaction. MSSPs handle any communication with the provider through online portals and emails. MDRs have teams of experts -- sometimes referred to as a security operations center (SOC) -- that can be reached through multiple channels in real time.
- Detection methods. Because of the human expertise component that MDRs offer, they can apply deeper analysis to alerts and detect novel threats. MSSPs are less involved in analysis, focusing more on known and frequently occurring threats using a rule-based system.
- Network visibility. MDRs can detect events and movement within a client network, whereas MSSPs focus mainly on perimeter.
- Resource allocation. MDR is beneficial for companies that prefer not to handle security internally and instead invest their financial resources in acquiring MDR services. However, classic managed security usually necessitates hiring a security team and administering an SOC.
- Notifications. Notifications are filtered with MDR, saving the team from having to address false positives. In contrast, MSSPs send out notifications for every security event regardless of its nature.
- Monitoring. MDR offers around-the-clock monitoring and cybersecurity services, providing continuous surveillance. MSSPs typically provide more constrained monitoring services.
- Technology types. MSSPs are good for managing foundational security technology such as firewalls and performing day-to-day security tasks. MDRs are more specialized services designed to handle complex modern networks and the new vulnerabilities they present.
Each option has its strengths and weaknesses. Companies can use both products in tandem to maximize the benefits.
Common features in MDR offerings
MDRs are relatively new. Each company differs somewhat in what they provide in their MDR offerings. Providers will typically focus on either network-, endpoint- or log-based technologies. A network-based MDR focuses on threats in a firewall, whereas an endpoint-based product works with antimalware software.
Regardless of the network level that the service works at, it unites reports from multiple technologies at that level to perform these functions:
- Threat detection, in which the SOC continuously monitors data and prioritizes alerts for analysis.
- Threat analysis, in which SOC personnel hone in on potential threats and determine the source and scope of the threat.
- Threat response, in which the provider notifies the client of an incident and offers their analysis recommendations for resolving the problem.
- Event triage, in which MDR services categorize and prioritize security events based on their criticality. By considering various factors, they create a list of security events to ensure that the most crucial incidents receive immediate attention.
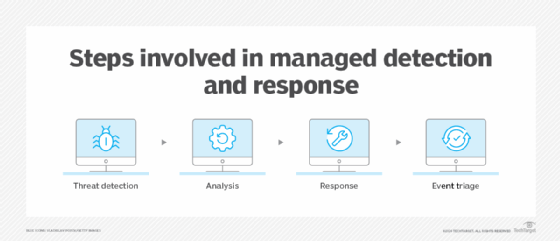
The step with the most variation between providers is the response step. Each provider decides the point at which their work ends, and the customer takes on the issue. Some providers might also offer additional features for a price, such as on-premises expert consultation or additional on-premises hardware.
When choosing a provider, customers should consider the following.
Organizational size
When looking for MDR providers, the size of the organization matters. For example, larger organizations may have more complex networks and a higher volume of security events. Therefore, they should look for an MDR provider capable of handling the scale and can detect and respond to incidents promptly.
Level of skill and competency
It's critical to select a provider with experience and knowledge in cybersecurity. Customers should also look for a company that provides onboarding assistance and client success services.
Technology and tools
The type of technology an MDR uses and whether they are up to date with the latest security tools and technologies is an important factor to consider when searching for a provider. Customers can assess the MDR provider's team's competence by looking at the type of security tools that they use.
Adherence to compliance
By understanding and verifying the compliance regulations that an MDR provider adheres to, an organization can make informed decisions, reduce regulatory risks and ensure that the chosen provider aligns with the specific requirements of their industry and geographic location.
Transparent communication
Effective communication is critical in the customer-MDR provider interaction. Customers should inquire about the provider's communication channels and protocols, both during ordinary operations and incident response. Transparency in communication is also vital, as the provider should be able to explain the steps of the MDR service and offer updates on the progress of the security measures.
A well-engineered MDR system can offer numerous benefits to any organization. Learn how to select the right MDR service and what to expect from an MDR provider.
