network slicing
What is network slicing?
Network slicing is a technique that creates multiple virtual networks on top of a shared physical network to provide greater flexibility in the use and allocation of network resources.
Network slicing is used most often in the discussion of 5G networks, in part because the 5G specification calls for network slicing as a fundamental capability, whereas 4G and earlier generations of cellular data services did not and could not support network slicing.
Each slice of a network can have its own logical topology, security rules and performance characteristics -- within the limits imposed by the underlying physical networks. Different slices can be dedicated to different purposes, such as ensuring a specific application or service gets priority access to capacity and delivery or isolating traffic for specific users or device classes.
The basics of network slicing
Slicing technologies on Ethernet networks are as old as virtual local area networks. The concept has been more fully realized with the rise of software-defined networking and, more recently, software-defined wide area networks (SD-WANs), which apply SDN concepts to wide area networking. SDN separates the network's control plane from the packet-handling data plane. The control plane can define virtual networks by defining packet-handling rules and pushing those rules out to the data plane devices for execution.
This control of the data plane applies to both physical and virtual network devices managed under the SDN controller, which is a physical switch in a rack or a virtual switch running in a cloud environment or on a hypervisor in the data center.
For some use cases, the network operator or the telecommunications provider wants or needs to dedicate network infrastructure to a specific slice of the network, such as assigning a virtual firewall to a specific virtual network instead of using a shared firewall. In some cases, this step is done to meet specific customer compliance or network security requirements. In other cases, network managers look to improve network performance or minimize the overhead of providing services. For example, network operators could deploy an instance of a low-cost or free firewall instead of paying for a more expensive one.
The flip side of slicing is aggregation. An SDN approach does enable aggregation of physical connectivity -- the melding of multiple physical connections into a switch, for example -- with the resulting pooled capacity then being made available for slicing.
How does network slicing work in 5G?
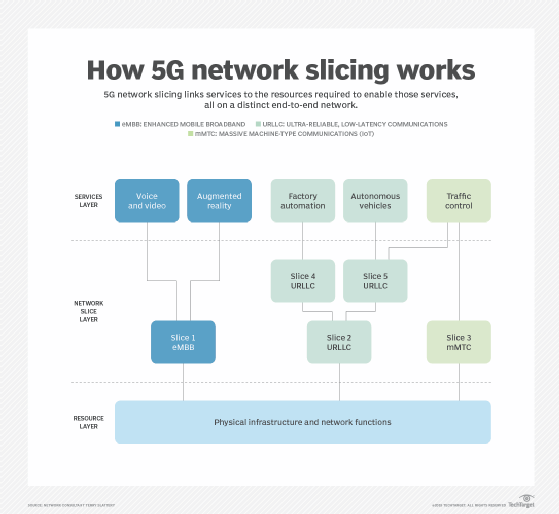
Network slicing is a key feature of 5G core architecture and applies the same principles of virtualization across the entire provider network architecture. These principles include radio access networks (RANs) and the supporting backhaul and carrier core networks that underlie 5G technology, including associated data center resources. Slicing enables service providers to create a variety of network slice architectures that deliver meaningful guarantees to customers regarding, say, a minimum amount of throughput for their connections or priority delivery of packets from specific types of devices or applications.
A 5G network operator can physically segregate traffic on different radio networks, slice a single network, or combine the capacity of multiple networks and slice the pooled resources. This enables 5G network operators to choose the characteristics needed to support their target levels of spectrum efficiency, traffic capacity and connection density, which is how many devices can connect from a given space.
5G service types -- high-level categories of network slice architecture -- that use slicing for differential handling of traffic include the following:
- Enhanced Mobile Broadband, or eMBB, provides mobile data access in one of three ways: to dense collections of users, to highly mobile users and to users spread over wide areas. It relies on features such as large arrays of multiple input, multiple output (MIMO) antennas and the combination of spectra, starting with conventional 4G wavelengths and stretching into the millimeter band.
- Massive Machine-Type Communications, or mMTC, services are built to serve massive numbers of devices in a small area with the expectation that they generate little data (about tens of bytes per second) and can tolerate high latency (up to 10 seconds on a round trip). Further, the specifications require that sending and receiving data require little power so that devices can have long battery lives. On a related note, the 5G New Radio specification calls for support of 1 million devices in 1 square kilometer.
- Ultra-Reliable Low-Latency Communications (URLLC) uses 5G to deliver secure communications with latencies of 1 millisecond (ms) and high reliability with low, or even zero, packet loss. It is achieved through a combination of physical device optimizations on MIMO antenna assemblies, simultaneous manipulation of multiple frequency bands, packet coding and processing techniques, and optimized signal handling.
Benefits of network slicing
For service providers, slicing -- in combination with virtual network functions -- is the key to "just right" services. Namely, on a base of generic wireless infrastructure and general-purpose compute and storage resources, service providers provision only as much capacity for specialized network services as is required to meet the needs of paying customers. Using built-in capabilities to slice capacity and using all virtual service platforms also mean that even complex and unique customer environments can be spun up in a short time.
For service providers, network slicing provides the following benefits:
- New revenue opportunities. Network slicking creates new revenue opportunities by lowering the barriers to trying out new service offerings. After specialized hardware is designed for a job, it does not need to be bought and then fully depreciated.
- Enhanced flexibility. Increased flexibility is achieved by enabling more kinds of services to be offered simultaneously since they don't require dedicated and specialized hardware.
- Easy scaling. Easier scaling is possible with network slicing since all the physical infrastructure is generic.
- Improved return on investment (ROI). Increased ROI is also likely since the ability to constantly try new things enables maximum use of resources.
- Customization. With network slicing, businesses can tailor networking requirements to certain workloads. For instance, the latency, bandwidth, quality of service and security needs of various departments and operations inside a company may differ and can be customized accordingly with network slicing.
- Support for emerging technologies. Network slicing is useful for emerging technologies and industries that need guaranteed network access, large capacity and low latency. For instance, it can support the internet of things (IoT), and it can facilitate the broad adoption of autonomous vehicles and growing industries, including telemedicine.
- Optimized radio access. RANs can now be customized for particular slices thanks to network slicing. This feature boosts overall network performance, lowers interference and optimizes the use of radio spectrum. Utilizing radio access that is optimized for particular services enables faster deployment.
Network slicing use cases
Network slicing supports use cases that focus on performance, capacity and security. Many use cases involve emerging IoT business models. Network slicing use cases include the following:
- Real-time performance. A company depending on a 5G network for autonomous vehicle management might contract for a mobile network slice with latencies under 5 ms and stringent guarantees of packet delivery on the minimum throughput required to ensure responsive control. The provider uses URLLC functionality to guarantee the slice on the lowest-latency equipment and paths between vehicles and cloud or edge resources and reserve enough capacity to meet the throughput target.
- Capacity. For a security monitoring system in a large auditorium, latency may not matter. However, the security company may want to buy guaranteed delivery of the camera data. In other words, the company wants its traffic to get 1.5 megabits per second of throughput per camera with no packets dropped ever. The provider might aggregate multiple connectivity and processing device options to meet the needs of this slice.
- Security. For a human health monitoring system in a metropolitan area, a hospital might want to isolate all traffic to and from pacemakers. This minimizes the risk of a leak of customer data and the threat of compromise of the control channel, so it requires a slice with single-user virtual resources.
- Media and entertainment. By offering specific slices for high-quality video streaming, virtual reality, and augmented reality applications, network slicing can improve the delivery of media and entertainment services. This guarantees a reliable and captivating user experience.
Business and enterprise possibilities
Enterprises and smaller businesses find slicing an attractive option on their own networks for both performance and security management, hence the rapid rise of SD-WAN and network segmentation technologies.
As 5G networks continue to mature and spread, slicing increases the utility of a wireless WAN (WWAN) and an enterprise wireless local area network (WLAN):
- WWAN. Before 5G, small branch offices depended on 4G Long-Term Evolution as backup connectivity in case their primary wired connections failed and, less often, used it as primary connectivity. 5G, with higher speeds and slicing, accelerates the adoption of the WWAN model and increases use as primary or sole connectivity since companies get meaningful service-level agreements that reflect the carriers' ability to control capacities and performance.
- WLAN. Those same capabilities for greater control increase the appeal of 5G as a replacement for private Wi-Fi-based WLANs. Traditionally, enterprises provision and manage a private network and deploy remote and mobile network access technologies. With 5G and slicing, many might instead use 5G only. Users have the same experience independent of location thanks to mobile broadband service via a private network slice integrated into the company WAN.
The combination of 5G and SD-WAN holds substantial potential for elevating network connectivity among remote employees. Examine the pros and cons of utilizing both technologies concurrently.