offensive security
What is offensive security?
Offensive security is the practice of actively seeking out vulnerabilities in an organization's cybersecurity. It often involves using similar tactics as attackers and might include red teaming, penetration testing and vulnerability assessments. Offensive security can be shortened to "OffSec."
In the past, offensive security referred to methods to actively slow down or to find information about attackers. This is no longer widely practiced due to modern security practices and changing threat landscape.

Why offensive security is important?
"No plan survives first contact with the enemy" is a common saying based on the words of military strategist Helmuth von Moltke the Elder. More succinctly, Mike Tyson once said "everyone has a plan until they get punched in the mouth." These quotes underline that having a cybersecurity plan is important, but until it is tested, it is unknown how much value it will have in the face of real cyberthreats.
Offensive security seeks to find any flaws in a cybersecurity plan before an attacker can. It does this by actively probing for weaknesses. This type of tested security is becoming increasingly important as attackers become more sophisticated and the threat landscape is widened to include internal systems, cloud services and connected third parties.
Incident response is an important part of modern cybersecurity. Offensive security operations are the best way to test that the detection and response mechanisms perform well and can respond to an active incident.
Offensive security testing can be done with computer security or physical security. Offensive cybersecurity operations test the resiliency of computer systems. Physical operations might test access control or use social engineering to try to gain access to a secure location.
Types of offensive security
There are several categories of offensive security. They are best executed by specialized teams, but internal security teams can also perform these types of security audits:
- Vulnerability scanning and vulnerability management passively search and catalog for issues in systems. Often it will be performed with a network vulnerability scanning tool that automatically checks devices against a list of known vulnerabilities. These tools can scan all devices in a network and produce a report of any issues found. Once identified these will be classified by severity and potentially remediated by internal teams. This data can then be fed into a vulnerability management software to track the findings and make informed risk analysis.
- Penetration testing actively seeks flaws. This can be done by an outside team hired to try to gain access to a system or network. It is much more thorough than a passive vulnerability scan because it seeks to find uncommon or actively exploitable flaws. Penetration testing reveals the problems and how to defend against them. Penetration testing is recommended by most security frameworks and some security standards. Some regulations require penetration testing; for example, PCI compliance requires yearly penetration testing.
- Red teaming/blue teaming is an active simulation of an attack by a group that will use the methods of hackers to try to gain access. Red teaming can be called an adversarial simulation. While penetration testing usually takes place over a shorter timeframe with defined targets, a red team will endeavor to do everything an attacker would do to gain access sometimes over weeks to months. A red team operation is usually done without informing the rest of the computer teams. Blue team is an internal security team that will respond to the red team attack and try to detect and thwart them.
- Penetration testing and red teaming are often categorized by how much knowledge the attacker possesses, and testing, such as black box, white box or gray box. In a black box scenario, the testers are given no prior knowledge of the target's systems and infrastructure; this most closely simulates an attack by an outside group. In a white box scenario, the attacker is given full knowledge and perhaps a level of access, this simulates an attack by a malicious insider. Gray box is somewhere in between, perhaps with limited credentials.

Steps in an offensive security operation
Careful planning is an important step in any offensive security operation. While offensive security can emulate the techniques and tactics of hackers, the goal is not to cause damage but instead to probe for weaknesses. These findings can then be reported and remediated using the following steps:
Define project scope. The auditors and customer work together to define what is and isn't included in the operation. This will include the timeframe and a discussion of what the client wishes to see during the operation. A contract will be signed to give the auditors permission to perform the audit.
Intelligence gathering and discovery. The auditors will usually spend time gathering intelligence about the client. This is often with passive reconnaissance, such as open source intelligence (OSINT), and through active probing of systems. They will catalog all found potential flaws and select one to exploit. During this phase the internal security teams might begin to see strange activity directed toward edge systems.
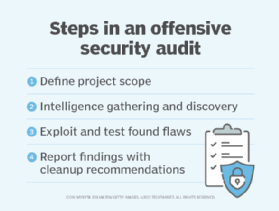
Exploitation and escalation. The auditors begin to exploit found flaws to gain access to systems. They will try to escalate their privilege in the systems and establish a way to maintain access to systems. At this point they will try to evade detection by internal teams while continuing to access increasingly secure data and systems.
Reporting and cleanup. The auditors will make a report of all their findings and potential remediation methods. This can include all accessed systems and data. It's often beneficial to have a post-mortem meeting with the internal teams. A cleanup will then be performed where any tools the auditors used are removed from systems, such as trojans or exploited accounts.
Offensive security frameworks
Open Web Application Security Project (OWASP) testing guides provides a penetration testing framework and a Payment Card Industry Data Security Standard (PCI DSS) guidance.
NIST Cybersecurity Framework has several guides, including a Technical Guide to Information Security Testing and Assessment NIST SP 800-115.
The Penetration Testing Execution Standard (PTES) is an open source standard developed by several security professionals.
Learn the difference between red teams versus blue teams versus purple teams when simulating attacks on enterprise networks. Read about 10 ways to prevent computer security threats from insiders. See how to prevent 12 cybersecurity risks of remote work. Check out how, when and why to use incident response tools, how to build an incident response plan and five ethical hacker certifications to consider.
