operation (computing)
What is an operation (computing)?
An operation, in computing, is an action that is carried out to accomplish a given task. There are five basic types of computer operations: inputting, processing, outputting, storing and controlling.
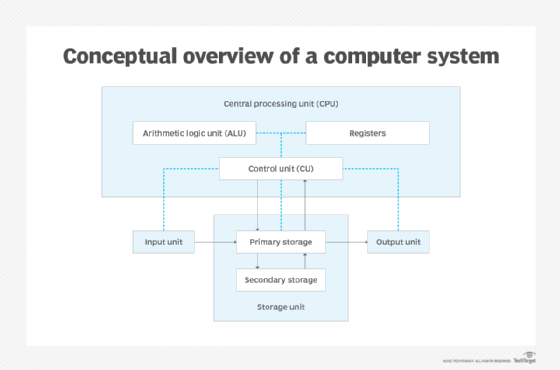
Computer operations are executed by the five primary functional units that make up a computer system. The units correspond directly to the five types of operations. They include the input unit, storage unit, output unit and two of the main components in the central processing unit (CPU) -- the arithmetic logic unit (ALU) and the control unit (CU).
The diagram below provides a conceptual overview of a computer system and its five primary units.
The black arrows represent the data flow, and the blue dotted lines represent the control flow. The computer system receives input instructions and data from users and programs. When the system first accepts the data, it stores the information in memory (primary storage) and then makes it available to the CPU for processing. The processing operation results in the generation of some type of output, which is delivered to the output unit where the information can be disseminated.
What is the input unit?
The input unit is a collection of devices that initiate input operations. The devices might include a keyboard, mouse, trackpad, scanner, microphone, card reader or some other type of device. Input devices enable users to send data and instructions to the computer for processing. These devices allow users to interface directly with the computer in real time or users can set up a device, such as motion detector, to initiate input operations automatically.
The input unit acts as a bridge between the outside world and the computer system. For each input operation, the input device must send the data and instructions in a binary format that the CPU understands. Input devices are divided into two broad categories: direct entry and indirect entry. Direct entry devices send data and instructions directly to the computer. Optical scanners and touchscreens are two examples of direct entry devices. Indirect entry devices, such as keyboards and joysticks, must first translate the input into a binary format, a process referred to as encoding.
What is the arithmetic logic unit?
When the computer system receives the binary data, it stores it in memory, where it can be accessed by the CPU for processing. A processor can only execute simple operations. To perform complex tasks, it must execute billions of individual operations per second.
One of the CPU's most important components is the ALU, which carries out the system's processing operations. The ALU performs arithmetic and logic operations on the operands based on the inputted instructions, which specify each step required to make the software do something.
The ALU performs arithmetic operations such as add, subtract, multiply, divide, increment and decrement. It can also perform logic operations such as AND, OR and Exclusive-OR. Logic operations rely on Boolean operators, which work with true/false values. The logic operations also use relational operators to perform comparisons. These include operators such as equal (=), less than (<) and greater than (>).
The ALU usually has direct input and output access to the process controller, main memory or RAM, and input and output devices. Inputs and outputs flow through the system bus. The input consists of an instruction word that contains an operation code, one or more operands, and sometimes a format code.
What is the output unit?
When the CPU has finished processing the inputted data, the computer system carries out a series of output operations that direct the processing results to the output unit. The output unit, like the input unit, is a collection of devices. In this case, however, they can receive and translate the data delivered through the output operations. Output devices might include monitors, speakers, printers, projectors, plotters or other devices.
The output operations deliver data in binary code. It is up to the device to make sense of this information and convert it to a usable format. Some output devices might include their own processor and memory resources to help reduce the load on the computer, improve local Performance or, if applicable, reduce network traffic. For example, laser printers often include processors and RAM.
What is the storage unit?
The storage unit, also called the memory unit, contains primary and secondary storage devices. Primary storage includes RAM and ROM. Secondary storage can include solid-state drives (SSDs), hard-disk drives (HDDs), optical devices, USB flash drives and other nonvolatile storage devices. Input, processing and output operations rely extensively on primary storage. Input data is stored in memory, the CPU uses memory when processing data, and processing output is staged to memory before being sent to the output unit. The process of storing and retrieving data requires carefully controlled storage operations that facilitate efficient and fast access to the data on the memory devices.
What is the control unit?
Control operations are responsible for coordinating all the other operations on the computer system. The CU carries out the control operations, ensuring that data is properly transferred, processed and stored. It retrieves and decodes each instruction in memory, and then uses this information to issue the signals necessary to coordinate operations across the computer system. The CU does not process or store data, but it controls all communications and synchronizes all operations. For this reason, it has access to all the other units on the computer system. To maintain this control, the CU includes multiple components, such as a timing unit, instruction decoder and control state generator.
See also: operand, computer instruction
