passive attack
What is a passive attack?
A passive attack is a network attack in which a system is monitored and sometimes scanned for open ports and vulnerabilities. The purpose of a passive attack is to gain information about the system being targeted; it does not involve any direct action on the target.
Passive attacks include active reconnaissance and passive reconnaissance. The word reconnaissance comes from the military term that refers to the act of exploring an enemy territory to gather information. In a computer security context, reconnaissance is the act of exploring a system or network in order to gather information before conducting a full attack.
These two types of attacks differ in the following ways:
- Active reconnaissance. The intruder engages with the target system to gather information about vulnerabilities. Attackers often use methods such as port scanning to learn which ports are open and what services are running on them.
- Passive reconnaissance. The intruder monitors the system for vulnerabilities without interaction for the sole purpose of gaining information. Often the attacker monitors a user's web session and then uses information retrieved from that session to conduct a future attack.
Types of passive attacks
Passive attacks can take various forms, including the following:
- Traffic analysis. This involves analyzing network traffic as it moves to and from the target systems. These types of attacks use statistical methods to analyze and interpret the patterns of communication exchanged over the network. These attacks can be performed on encrypted network traffic, but they are more common on unencrypted traffic.
- Eavesdropping. Eavesdropping occurs when an attacker intercepts sensitive information by listening to phone calls or reading unencrypted messages exchanged in a communication medium. Although eavesdropping is similar to snooping, snooping is limited to gaining access to data during transmission.
- Footprinting. This is the process of gathering as much information as possible about the target company's network, hardware, software and employees. Footprinting gathers information on the target, such as IP address, domain name system information and employee ID. Footprinting is also the first step in gathering information for a penetration test.
- Spying. An intruder might masquerade as an authorized network user and spy without interaction. With that access, an intruder might monitor network traffic by setting the network adapter to promiscuous mode to capture all encrypted data traffic on a network.
- War driving. War driving detects vulnerable Wi-Fi networks by scanning them from nearby locations with a portable antenna. This type of passive attack is typically carried out from a moving vehicle. Hackers sometimes plot out areas with vulnerabilities on a map using a GPS. War driving can be done just to steal an internet connection or as a preliminary activity for a future attack.
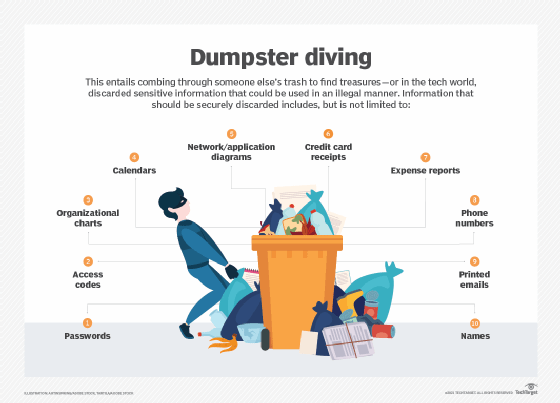
- Dumpster diving. In this type of attack, intruders look for information stored on discarded devices or even passwords in trash bins. The intruders can then use this information to facilitate covert entry to a network or system.
What is the difference between a passive and an active security attack?
With an active attack, the intruder attempts to alter data on the target system or data in transit to or from the target system. During an active attack, an attacker tries to exploit a vulnerability to hack into a system or to gain access to a user's data. An active attacker interacts with the target before extracting information from the target or making changes to it. In contrast, a passive attacker intercepts network traffic or examines files from the target without any direct interaction.
Interactions in an active attack typically occur by way of impersonation, modification of messages, session replays or denial of service attacks. Passive attacks often precede active attacks, as an attacker may use information gathered to conduct a future active attack.
How to avoid passive attacks
A passive attack is difficult to track because it often does not leave any traces of the attacker's interference, and it can be hard to determine if the system has been compromised. As a result, passive attacks are a type of data breach that go largely unnoticed. However, there are some preventive measures that can help enterprises avoid passive attacks.
- Encrypt data. Encryption is a security technique that obscures data from everyone but the recipient. When data is encrypted, anyone who intercepts it will only see an incomprehensible combination of characters. The best way to prevent data breaches is to encrypt data so that it is protected during the transmission and storage stages. Encryption is not a panacea, however, and is not effective for all threats. It is also not a substitute for proper network security. Encryption uses the following two types of cryptography algorithm:
- Symmetric encryption. Symmetric encryption is used to protect data using a single cryptographic key. Both the sender and the receiver must have the exact same key. As long as both parties have copies of the key, they can use it to encrypt and decrypt messages.
- Asymmetric -- or public key -- encryption. More secure than symmetric encryption, public key encryption uses a pair of related keys, one of which is secret or private and the other of which is public. The public key is made available to anyone who wishes to send an encrypted message, and it may be freely distributed. The private key is only accessible to the person authorized to decrypt messages sent with the public key.
- Keep sensitive information private. Do not share private information publicly. Attackers can use this information to hack into a private network.
What's the difference between data protection, data security and data privacy? Compare these three areas to learn how each keeps sensitive data safe.