targeted ad (targeted advertising)
What is a targeted ad (targeted advertising)?
A targeted ad, or targeted advertising, is a method of displaying advertisements to a specific group of people based on their demographics, behavior, interests or other criteria. Targeted advertising ensures that the ad content reaches the individuals most likely to be interested in the product or service being promoted.
With most potential customers now online in some way, businesses vying for the attention of their ideal customers must find unique ways to target them or risk having their product or service get lost in the noise of the online marketplace.
Targeted advertising is among the most effective ways of reaching the right audience and it can address multiple stages of demand generation.
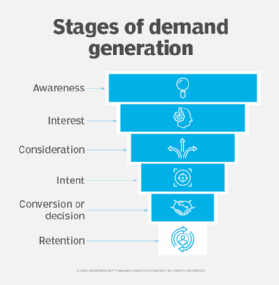
How targeted advertising works
Targeted advertising is a meticulous process that leverages data to ensure advertisements are presented to audiences most likely to resonate with the content. The intricacies of the approach stem from several key steps:
- Data collection: Initially, data about users, including browsing history, purchases, and even social media interactions, is gathered through their online activities.
- User profiling: Once enough data is collected, customer profiles are created, categorizing individuals based on demographics, online behavior, interests, and preferences.
- Ad creation: Advertisers then craft tailored ads designed to appeal specifically to these segmented profiles.
- Ad serving: Sophisticated algorithms determine when and where these ads will be displayed. This decision is based on the match between the user's profile and the criteria set by advertisers.
- Feedback loop: After ads are displayed, further data is collected on customer engagement (clicks, views, purchases). This feedback helps refine user profiles and makes future ad targeting even more precise.
Targeted advertising creates, in essence, a dynamic ecosystem where user behavior continuously informs and refines the ads they see, ensuring a higher probability of engagement and conversion.
Benefits of targeted advertising
Targeted advertising offers tailored strategies to connect brands with consumers effectively. Some of its salient benefits include the following:
- Increased engagement: By catering to specific interests and needs, targeted ads often yield higher user interaction.
- Personalization potential: These ads can be tailored to fit each user's preferences, ensuring a more relevant, customized experience.
- Enhanced brand awareness: By consistently presenting pertinent ads to potential consumers, brands can solidify their image and position in the market.
- Improved brand perception: Offering content that resonates with the audience can elevate a brand's perception and trustworthiness.
Platforms for targeted advertising
Choosing the right platform to implement targeted advertising can be the linchpin of a campaign's success. The platform your business ultimately uses will depend largely on your target market and where they prefer to consume content.
Over recent years, certain platforms have risen in prominence:
- Google: Renowned for its vast reach, Google provides a comprehensive suite for advertisers, encompassing search to display networks.
- Facebook: With its extensive user base, Facebook offers in-depth user analytics, making it a treasure trove for targeted advertising.
- Instagram: As a visually-driven platform, Instagram caters especially to brands with strong visual content.
- TikTok: The emerging titan in the social media realm, TikTok is gaining traction for its unique, short-form video content and its appeal to younger demographics.
By harnessing the power of targeted advertising and leveraging the right platforms, businesses can create more impactful, effective marketing campaigns that deliver more precisely relevant, engaging content and achieve a higher return on investment for their advertising campaigns.
Explore the top four SEO marketing challenges and four digital marketing best practices for businesses. See how to incorporate social media into SEO strategies and check out the different types of marketing personalization.
