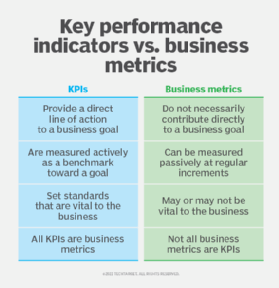
What is ROI? How to calculate return on investment
Return on investment, or ROI, is a mathematical formula that investors can use to evaluate their investments and judge how well a particular investment has performed compared to others. An ROI calculation is sometimes used with other approaches to develop a business case for a given proposal. The overall ROI for an enterprise is used as a way to grade how well a company is managed.
ROI measures the return on an investment relative to its cost. The formula for ROI is straightforward, but its application can be varied, reflecting its broad applicability across different types of investments, including digital marketing, social media campaigns and technology projects.
Sometimes, an ROI calculation accompanies other approaches to develop a business case for a given proposal. The overall ROI for an enterprise is a way to grade how well a company is managed.
If an enterprise has immediate objectives, such as getting market revenue share, building infrastructure or positioning itself for sale, ROI might be measured in terms of meeting one or more of these objectives rather than immediate profit or cost savings.
How do you calculate ROI?
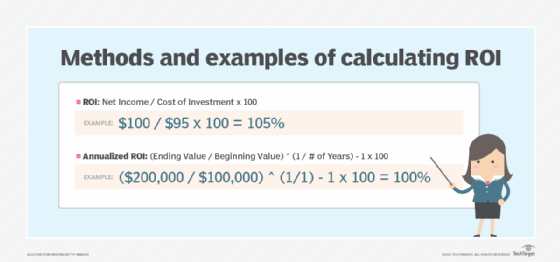
Traditionally, ROI is calculated by dividing the net income from an investment by the original cost of the investment, the result of which is expressed as a percentage using the following formula.
ROI = net income ÷ cost of investment × 100
This method remains fundamental in assessing the profitability of traditional investments.
Consider someone who invested $90 into a business venture and spent an additional $10 researching the venture. The investor's total cost is $100. If the venture generated $300 in revenue but had $100 in personnel and regulatory costs, then net profits would be $200.
ROI is $200 divided by $100 for a quotient of 2. Because ROI is most often expressed as a percentage, the quotient is converted to a percentage by multiplying it by 100. This investment's ROI is 2 multiplied by 100, or 200%.
Here's another example: An investor puts $10,000 into a venture with no fees or associated costs. The company's net profits are $15,000. The investor made $5,000. It is significantly more than the $200 in net profits generated in the first example. However, the ROI is less: $15,000 divided by $10,000 equals 1.5. Multiplying that by 100 yields an ROI of 150%.
Although the first investment strategy produced fewer dollars, the higher ROI indicates it was a more productive investment.
Another way to calculate ROI is by using the following formula:
ROI = investment gain ÷ investment base
There are numerous other ways to calculate ROI. When discussing or comparing ROIs between departments or businesses, it is important to clarify which equation determined the percentage. Each equation might measure a specific set of investments.
Digital marketing and social media investments
In the digital realm, ROI calculations often incorporate metrics such as customer acquisition cost, lifetime value of a customer, conversion rates and engagement rates. Tools and platforms now offer sophisticated analytics to track these metrics, allowing a more nuanced analysis of digital marketing efforts.
ROI and technology investments
ROI for technology projects can include savings from increased efficiency, the value of time saved and the revenue generated from new technological capabilities. Calculations often factor in implementation costs, including training and change management, to provide a comprehensive view of the investment's return.
How do you interpret ROI calculations?
ROI can be used to gauge different metrics, all of which help illuminate business profitability. To calculate ROI with maximum accuracy, total returns and total costs should be measured.
When ROI calculations have a positive return percentage, this means the business -- or the ROI metric being measured -- is profitable. If the calculation has a negative ROI percentage, that means the business -- or metric being measured -- owes more money than what is being earned. In short, if the percentage is positive, the returns exceed the total cost. If the percentage is negative, the investment is generating a loss.
What is ROI used for?
ROI is useful for evaluating various investment decisions, comparing them to their initial cost. Businesses also use ROI calculations when evaluating future or prior investments.
Individuals can calculate the ROI to judge their own personal investments and compare one investment -- whether it is a stock holding or a financial stake in a small company -- against another in their own investment portfolios.
What are examples of ROI calculations?
Calculating the investment figures for each piece of the ROI equation can sometimes get complicated for businesses.
If a company wants to invest in deploying new computers, it must consider a variety of deployment costs: the actual price of the computers, tax and shipping costs, consulting fees or support costs paid to purchase, and setup and maintenance costs. Then the business should calculate net profit over a set period. These net profits could include hard dollar amounts coming from increased productivity and lower maintenance costs compared to the previous computers.
The business could then calculate the ROI when evaluating two different types of computers using anticipated costs and projected gains to determine which ROI is higher. Which computer represents the better investment: Investment A or Investment B?
The business could also calculate the ROI at the end of the set period using actual figures for total net income and total cost of investment. Actual ROI can then be compared to projected ROI to help evaluate whether the computer implementation met expectations.
Incorporating risk into ROI calculations
Investments carry varying levels of risk, which traditional ROI calculations might not fully capture. Adjusting ROI calculations for risk can provide a more nuanced understanding of an investment's potential.
Metrics such as risk-adjusted return on capital (RAROC) help businesses compare investments by adjusting returns based on the risk involved, facilitating a more informed decision that accounts for the investment's risk profile.
What are the benefits of ROI?
Benefits of ROI ratios include the following:
- Ease of calculation. Few figures are needed to complete the calculation, all of which should be available in financial statements or balance sheets.
- Comparative analysis capability. Because of its widespread use and ease of calculation, more comparisons can be made for investment returns between organizations.
- Measurement of profitability. ROI relates to net income for investments made in a specific business unit. This provides a better measure of profitability by company or team.
What are the limitations of ROI?
ROI is one of the most common investment and profitability ratios used today. However, it does have some drawbacks:
- Inability to consider time in the equation. On the surface, the higher ROI seems like the better investment. But an investment that takes 10 years to produce a higher ROI is less worthwhile than an investment that takes just one year to produce a slightly lower ROI. Time value of money (TVM) is the concept that money available at the present time is worth more than the same amount in the future due to its potential earning capacity.
- ROI calculations can differ between businesses. Because there are different equations to calculate ROI, not every business uses the same one, making the comparison between investments unequal and potentially irrelevant.
- Managers might only select investments with larger ROIs. Some investments with lower ROIs might still increase the value of a business. But suboptimal choices could lead to poor allocation of resources.
- No way to account for nonfinancial benefits. Using the ROI for new computers as an example, a business can use specific dollar amounts to calculate the net profit and total costs to come up with ROI. However, calculating the value of improved worker morale from getting new computers is difficult. Businesses can, however, calculate ROIs for such intangible benefits by labeling these calculations as soft ROIs, while calculations made with tangible amounts are hard ROIs.
What are the alternatives to ROI?
There are some alternative ROI measures businesses use to varying degrees.
To address the TVM issue, analysts might use net present value (NPV), which considers TVM by discounting future cash flows to their present value, or internal rate of return, which is the interest rate at which the NPV of all the cash flows from a project or investment equals zero.
Annualized ROI is a form of ROI considers the length of time a stakeholder has the investment. The following is the formula.
Annualized ROI = ((final value of investment − initial value of investment) ÷ initial value of investment) × 100
Likewise, the annual performance rate can be calculated using the following formula.
((P + G) ÷ P) ^ (1 ÷ n) − 1
In this formula, P equals initial investment, G equals gains or losses, and n equals the number of years the investment is held.
Social ROI (SROI) is outcome-based and considers the broader impact of economic, environmental and social value. It translates these outcomes into tangible dollar values. The following formula is used to calculate SROI.
SROI = net present value of benefits ÷ net present value of investment
Marketing statistics ROI determines the effectiveness of a marketing campaign strategy or marketing program. A basic calculation uses the following formula.
(sales growth − marketing cost) ÷ marketing cost
Social media statistics ROI determines the effectiveness of a social media campaign and can include how many views or likes are generated. A simple calculation to measure the time, money and resources that went into social media ROI by revenue uses the following formula:
(value ÷ total investment) × 100
ROI is a versatile, powerful metric for evaluating investment efficiency. However, as the business landscape evolves, so must the methodologies for calculating ROI.
By incorporating digital metrics, adjusting for TVM and risk, and considering sector-specific factors, businesses can gain a deeper understanding of their investments' true value. Additionally, exploring alternative metrics can offer broader insights, particularly for investments where traditional ROI does not capture the full spectrum of value generated.
A compelling ROI is critical to justify and secure funding for digital transformation projects in a rapidly changing business landscape with competing priorities. Explore tips to measure and improve digital transformation ROI.








