segregation of duties (SoD)
What is segregation of duties (SoD)?
Segregation of duties (SoD) is an internal control designed to prevent error and fraud by ensuring that at least two individuals are responsible for the separate parts of any task. SoD involves breaking down tasks that might reasonably be completed by a single individual into multiple tasks so that no one person is solely in control.
Segregation of duties is also known as separation of duties and is an essential element of an enterprise control system. The idea is to assign different parts of a task or transaction to different people to prevent any one person from gaining sole or excessive control and then misusing that control for nefarious or unauthorized purposes, such as perpetrating fraud or embezzling company funds.
Payroll management is a common area where segregation of duties is applied. In this administrative area, fraud and error are both common risks that segregating of responsibilities and tasks is meant to minimize. When segregating duties in payroll, it is common to have one employee responsible for the accounting portion of the job and another responsible for signing off on checks or authorizing funds disbursal.

The need for segregation of duties
The basis of SoD is the understanding that running a business should not be a single-person job. No one person should have the power or control to perform any kind of task that may lead to fraudulent or criminal activity that could damage the company. Segregation of duties is based on the idea of shared responsibilities, wherein the critical functions of a key process are dispersed to more than one person or department to mitigate the risk of fraud or other unethical behaviors. SoD is an important element of both enterprise risk management and compliance with laws such as the Sarbanes-Oxley Act of 2002 (SOX).
Segregating duties prevents the abuse of control and any consequent unscrupulous activity. Thus, separating the duties of critical processes among multiple personnel reduces the chances that any one employee or third party -- in isolation or by colluding with others -- could successfully accomplish any of the following:
- stealing funds from the organization;
- engaging in corporate espionage;
- launching some kind of revenge campaign due to perceived unfair dismissal, demotion or other alleged mistreatment; or
- falsifying financial records to satisfy stakeholders, meet earnings forecasts or artificially inflate the company's stock prices.
Common examples of segregation of duties in enterprise settings
Segregation of duties is a common concept in financial and accounting processes. Payroll is one example where the segregation of duties works well and is even desirable.
Another example is in a warehouse, where the person receiving goods from a supplier and the person authorizing payment to the supplier are two different employees. Similarly, the person maintaining inventory records does not physically control the inventory, which reduces the possibility of inventory theft or incorrect reporting.
A third example is within the real estate business, where the person selling a property or other fixed asset to a customer cannot record the sale or collect the payment from the customer. Since a different person is in charge of recording the sale and receiving payment, the separation of duties ensures that the person completing the sale cannot take an illegal cut from customers or deny the organization the full revenue from the sale of the asset.
Yet another example is in software development. A developer creates the code but doesn't have the authority to also deploy it into production. Someone else reviews and approves the code and then moves it into production. The idea is to prevent the release of unauthorized code, whether it's done maliciously or accidentally.
The following are some other examples of SoD applications:
- transaction authorizations or approvals;
- receiving and maintaining asset custody;
- recording transactions;
- reconciliation activities related to bank statements, checking accounts and booking entries to the general ledger;
- depositing cash; and
- approving timecards or timesheets.
In general, organizations can enforce SoD in any financial, IT, cybersecurity, software or other process/business function that can have a critical impact on an enterprise's business, revenues, reputation or customer relationships.
Challenges and drawbacks of segregation of duties
Segregation of duties improves security and reduces the possibility of someone misusing the control they have in a process for unethical purposes. On the flip side, breaking tasks down into separate components can negatively impact business efficiency. When sacrificing efficiency isn't an option, companies must live with the tradeoff of weaker control and the greater risk of fraud because the segregation of duties cannot be implemented or has been reduced.
SoD can also increase costs, process complexity and staffing requirements. As a result, most organizations apply SoD to only the most vulnerable or mission-critical elements of the business. Those are the areas where the risk of fraud and theft is highest and has the greatest chance of negatively impacting the organization's finances, security, reputation or compliance posture.
Moreover, smaller organizations may find it more difficult to accomplish the segregation of duties because there are fewer people available to take on different parts of a task. In small companies, one person may be in charge of an entire process, such as payroll, where a single employee handles both accounting and check sign-off.
Important concepts in segregation of duties
There are two important concepts in segregation of duties: SoD conflicts and SoD violations.
SoD conflicts. When an individual can potentially act in their own interest and against the company's interests, it can result in an SoD conflict. This simply means that they have multiple roles in a process, which allows them to perform a combination of important activities that could potentially harm the integrity of the process and, ultimately, the organization.
To prevent such issues, organizations should check for and analyze potential SoD conflicts. Strong controls should be implemented to prevent conflicts and to protect the company from individuals engaging in criminal activity. One way to prevent SoD conflicts is to implement role-based access control. An authorized person should analyze each role for both intra-role and inter-role SoD overlaps.
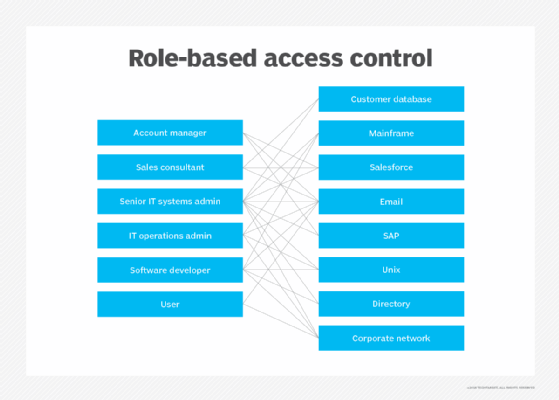
SoD violations. An SoD violation occurs when an employee abuses their role and access -- usually deliberately -- to perform a prohibited action. The prohibition may be in place due to internal company policy or an external industry regulation. A violation typically occurs when the user has or gains control over more process steps than they are allowed and then misuses that access for their own benefit.
For example, an organization may have a rule that the person approving timesheets is not allowed to also distribute paychecks. But when someone takes advantage of a control weakness to do both activities for fraudulent purposes, it becomes an SoD violation.
An example of a violation due to an external regulation is a senior leader, such as a CEO or CFO, manipulating financial statements in violation of SOX regulations; this can result in hefty fines for the company and a prison sentence for that employee.
The segregation of duties matrix
Implementing SoD can be a complex endeavor. Compliance managers reduce the complexity with a segregation of duties matrix. The matrix enables managers to clearly separate the various roles, responsibilities and risks in the organization. They can also identify potential conflicts and resolve them before any potential damage to the organization occurs.
The SoD matrix plots user roles on both the X and Y axes to clearly show SoD conflicts. It also maps activities and duties to roles within the workflow to help compliance teams segregate incompatible duties.
Below is an example of an SoD matrix for an employee compensation process, where a checkmark signifies that the role has responsibility for the task.
| Procedure/ function |
User group (role) | Hire employee | Change compensation | Change benefits | Create paycheck |
| Hire employee | 1 | √ | |||
| Change compensation | 2 | √ | √ | ||
| Change benefits | 3 | √ | √ | ||
| Create paycheck | 4 | √ |
In the matrix above, the person in charge of hiring employees cannot also be in charge of changing compensation or creating paychecks. Similarly, the person in charge of changing benefits cannot hire employees.
Here's another example of an SoD matrix for a software development process.
| Procedure/ function |
User group (role) | Develop software | Test software | Make data backups | Push code to production |
| Develop software | 1 | √ | |||
| Test software | 2 | √ | |||
| Make data backups | 3 | √ | |||
| Push code to production | 4 | √ |
The software developer is not allowed to test software, push the code to production or make data backups. Similarly, the person who pushes code to production cannot carry out the other three tasks.
Organizations can create SoD matrices by hand or with spreadsheet software, such as Excel. However, they are most commonly generated automatically using enterprise resource planning (ERP) software.
2 approaches to the SoD matrix from ISACA
Diagrams and flowcharts provide a good level of detail in SoD matrices. But sometimes these representations don't correctly match employee tasks, making it harder to identify role/activity inconsistencies or potential SoD conflicts. ISACA suggests two options to create more detailed and useful SoD matrices:
- Group or delete activities.
- Keep all activities and clearly label all SoD conflicts.
Option 1 reduces the size of the matrix and enables personnel to focus on potential SoD conflicts. The downside is that it can introduce errors and false positives, which may affect the SoD analysis and its outcomes. Option 2 creates a huge matrix but provides a more accurate visual representation of existing processes and personnel roles/activities.
See also: fraud detection, compensating control, four eyes principle, risk avoidance, corporate governance, accounting error, regulatory compliance, compliance burden.
