computer hardware
What is computer hardware?
Computer hardware is a collective term used to describe any of the physical components of an analog or digital computer. The term hardware distinguishes the tangible aspects of a computing device from software, which consists of written, machine-readable instructions or programs that tell physical components what to do and when to execute the instructions.
Hardware and software are complementary. A computing device can function efficiently and produce useful output only when both hardware and software work together appropriately.
Computer hardware can be categorized as being either internal or external components. Generally, internal hardware components are those necessary for the proper functioning of the computer, while external hardware components are attached to the computer to add or enhance functionality.
What are internal computer hardware components?
Internal components collectively process or store the instructions delivered by the program or operating system (OS). These include the following:
- Motherboard. This is a printed circuit board that holds the central processing unit (CPU) and other essential internal hardware and functions as the central hub that all other hardware components run through.
- CPU. The CPU is the brain of the computer that processes and executes digital instructions from various programs; its clock speed determines the computer's performance and efficiency in processing data.
- RAM. RAM -- or dynamic RAM -- is temporary memory storage that makes information immediately accessible to programs; RAM is volatile memory, so stored data is cleared when the computer powers off.
- Hard drive. Hard disk drives are physical storage devices that store both permanent and temporary data in different formats, including programs, OSes, device files, photos, etc.
- Solid-state drive (SSD). SSDs are solid-state storage devices based on NAND flash memory technology; SSDs are non-volatile, so they can safely store data even when the computer is powered down.
- Optical drive. Optical drives typically reside in an on-device drive bay; they enable the computer to read and interact with nonmagnetic external media, such as compact disc read-only memory or digital video discs.
- Heat sink. This is a passive piece of hardware that draws heat away from components to regulate/reduce their temperature to help ensure they continue to function properly. Typically, a heat sink is installed directly atop the CPU, which produces the most heat among internal components.
- Graphics processing unit. This chip-based device processes graphical data and often functions as an extension to the main CPU.
- Network interface card (NIC). A NIC is a circuit board or chip that enables the computer to connect to a network; also known as a network adapter or local area network adapter, it typically supports connection to an Ethernet network.
Other computing components, such as USB ports, power supplies, transistors and chips, are also types of internal hardware.
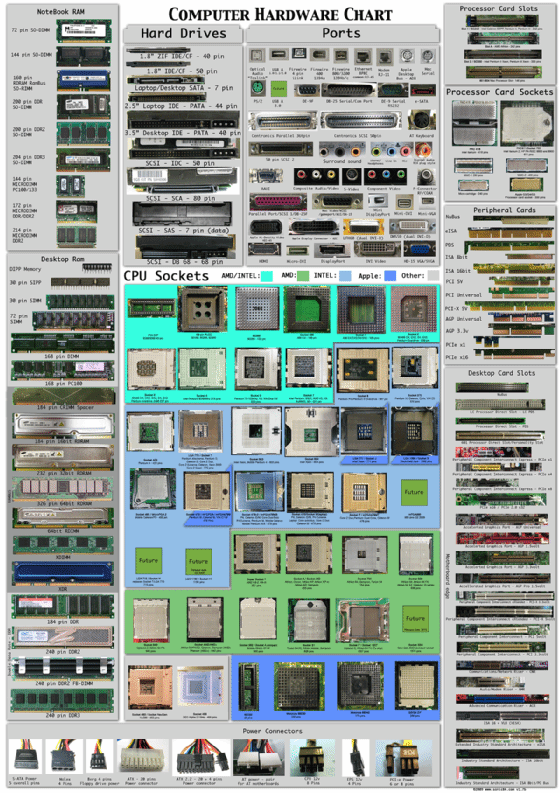
This computer hardware chart below illustrates what typical internal computer hardware components look like.
What are external hardware components?
External hardware components, also called peripheral components, are those items that are often externally connected to the computer to control either input or output functions. These hardware devices are designed to either provide instructions to the software (input) or render results from its execution (output).
Common input hardware components include the following:
- Mouse. A mouse is a hand-held pointing device that moves a cursor around a computer screen and enables interaction with objects on the screen. It may be wired or wireless.
- Keyboard. A keyboard is an input device featuring a standard QWERTY keyset that enables users to input text, numbers or special characters.
- Microphone. A microphone is a device that translates sound waves into electrical signals and supports computer-based audio communications.
- Camera. A camera captures visual images and streams them to the computer or through a computer to a network device.
- Touchpad. A touchpad is an input device, external or built into a laptop, used to control the pointer on a display screen. It is typically an alternative to an external mouse.
- USB flash drive. A USB flash drive is an external, removable storage device that uses flash memory and interfaces with a computer through a USB port.
- Memory card. A memory card is a type of portable external storage media, such as a CompactFlash card, used to store media or data files.
Other input hardware components include joysticks, styluses and scanners.
Examples of output hardware components include the following:
- Monitor. A monitor is an output device similar to a TV screen that displays information, documents or images generated by the computing device.
- Printer. Printers render electronic data from a computer into printed material.
- Speaker. A speaker is an external audio output device that connects to a computer to generate a sound output.
- Headphones, earphones, earbuds. Similar to speakers, these devices provide audio output that's audible only to a single listener.
Hardware vs. software
Hardware refers to the computer's tangible components or delivery systems that store and run the written instructions provided by the software. The software is the intangible part of the device that lets the user interact with the hardware and command it to perform specific tasks. Computer software includes the following:
- OS and related utilities;
- programs that control certain computer functions; and
- applications that usually perform operations on user-supplied data.
On mobile devices and laptop computers, virtual keyboards are also considered software because they're not physical.
Since the software and hardware depend on each other to enable a computer to produce useful output, the software must be designed to work properly with the hardware.
The presence of malicious software, or malware, such as viruses, Trojan horses, spyware and worms, can have a huge effect on computer programs and a system's OS. Hardware is not affected by malware, though.
However, malware can affect the system in other ways. For example, it can consume a large portion of the computer's memory or even replicate itself to fill the device's hard drive. This slows down the computer and may also prevent legitimate programs from running. Malware can also prevent users from accessing the files in the computer's hardware storage.

What is hardware virtualization?
Hardware virtualization is the abstraction of physical computing resources from the software that uses those resources. Simply put, when software is used to create virtual versions of hardware instead of using physical, tangible hardware components for some computing function, it is known as hardware virtualization.
Sometimes referred to as platform or server virtualization, hardware virtualization is executed on a particular hardware platform by host software. It requires a virtual machine manager called a hypervisor that creates virtual versions of internal hardware. This enables the hardware resources of one physical machine to be shared among OSes and applications and to be used more efficiently.
In cloud computing, hardware virtualization is often associated with infrastructure as a service (IaaS), a delivery model that provides hardware resources over high-speed internet. A cloud service provider (CSP), such as Amazon Web Services or Microsoft Azure, hosts all the hardware components that are traditionally present in an on-premises data center, including servers, storage and networking hardware, as well the software that makes virtualization possible.
This makes IaaS and CSPs different from hardware as a service (HaaS) provider that hosts only hardware but not software. Typically, an IaaS provider also supplies a range of services to accompany infrastructure components, such as the following:
- billing
- monitoring
- log access
- security
- load balancing
- clustering
Some CSPs also provide storage resiliency services, such as automated backup, replication and disaster recovery.
What is hardware as a service?
While it's common for individuals or businesses to purchase computer hardware and then periodically replace or upgrade it, they can also lease physical and virtual hardware from a service provider. The provider then becomes responsible for keeping hardware up to date, including its various physical components and the software running on it.
This is known as the HaaS model.
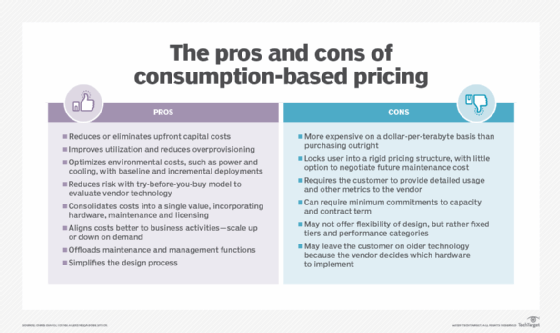
The biggest advantage of HaaS is that it reduces the costs of hardware purchases and maintenance, enabling organizations to shift from a capital expense budget to a generally less expensive operating expense budget. Also, since most HaaS offerings are based on a pay-as-you-go model, it makes it easier for organizations to control costs, while still having access to the hardware they need for their operational and business continuity.
In HaaS, physical components that belong to a managed service provider (MSP) are installed at a customer's site. A service-level agreement (SLA) defines the responsibilities of both parties.
The customer may either pay a monthly fee for using the MSP's hardware, or its use may be incorporated into the MSP's fee structure for installing, monitoring and maintaining the hardware. Either way, if the hardware breaks down or becomes outdated, the MSP is responsible for repairing or replacing it.
Depending upon the terms of the SLA, decommissioning hardware may include wiping proprietary data, physically destroying hard drives and certifying that old equipment has been recycled legally.