software audit
What is a software audit?
A software audit is an internal or external review of a software program to check its quality, progress or adherence to plans, standards and regulations. The process is conducted by either internal teams or by one or more independent auditors.
Software audits may be conducted for many reasons, including the following:
- to track and report software use, including frequency and who is using the software;
- to verify licensing compliance;
- to monitor for quality assurance (QA);
- to comply with industry standards; and
- to meet legal requirements.
Software development companies usually contract with third-party reviewers and teams to provide independent verification of a software program's compliance with development plans, industry standards, best practices and legal practices. Compliance audits may focus on adherence to IEEE standards or legal regulatory compliance. This kind of audit focus is especially important in the case of software used in critical infrastructure and key resources.
Instead of focusing on a software's technical quality, a software audit focuses on compliance of products or processes. They are an important part in evaluating if a software product or process adheres to regulations, standards and procedures.
Software audits serve a vital purpose to an organization. But they can also disrupt a company's development and may place a financial strain on a project because of unbudgeted costs. Teams and management may be required to consult with auditors to ensure the process is complete and accurate. The involved consultation can take away from time spent on work. Organizations should refrain from overdoing audits, and executives should understand how, why and when audits are conducted so they can best prepare for them.
Why are software audits necessary?
Internal audits can help an organization improve its efficiency by reducing the number of inactive or expired licenses and finding problems before they can become licensing or regulatory issues in a third-party review. An external, or third-party, review generally focuses on software that is being used beyond licensed rights and can help identify compliance gaps. These different priorities mean it is prudent for an organization to conduct an internal review before an external audit.
If an internal audit is done, the auditor the organization selects must be independent and unbiased. The auditors then determine if there are any violations, such as piracy. For example, the organization may have bought one software license but installed copies of the software on several devices.
Internally, software audits help organizations gain a reality check on their current state of affairs surrounding the use of software. The audits can help ensure the software an organization uses is up to date and is working as intended.
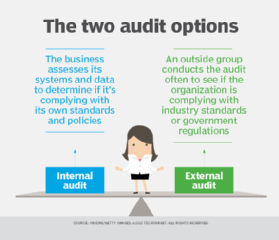
Software audits are conducted when an organization believes that it may be in violation of its user agreements. The organization can start a software audit when licensing compliance needs to be verified, to monitor QA, to ensure licenses are all current and up to date, and to ensure industry standards are still being complied with. Software audits also help uncover any unused tools with current licenses. Removing unused licensed software can help save an organization money. If an organization experiences a lack of visibility or software process bottlenecks, then a software audit acts as a health check for the software being audited.
How to conduct a software audit
Software audits take roughly 60 working days to complete, and an IT department could be asked to undergo up to three audits a year.
A software vendor or software publisher may communicate its intent to begin an audit through a formal mailed letter. The initiator of the audit may be anyone. This includes a manager, an organization representative, a customer or a third party. At an early stage, the audit personnel are chosen, and they decide on follow-up actions.
Software auditor participants include the audited organization, auditor and recorder. The audited organization works with the auditors to provide all the information the auditors may need to complete their tasks. The auditor is someone who examines the software products outlined in an audit plan, documents observations and provides recommended corrective measures. The recorder is a party that takes note of action items, anomalies and corrective actions. Recorders also document the audit team's recommendations.
Software audits follow an audit plan created by an audit team. The plan should outline the audit's objective and include further goals or obligations. Software audits include an audit of hardware, virtualization and software development inventory, as well as user data. Audited hardware is any device that is used in the organization or the software being audited. This includes every important detail surrounding the organization's hardware equipment.
Virtualization inventory under audit should have documented information about virtual environments and virtual servers that run on physical machines. Virtual machines that can migrate from one physical host to another should also be examined.
Software deployment inventory is a list of software that runs a device. The software vendor's name, product name, its edition and version should all be recorded.
User data collected is generally accessed by Active Directory, since it contains information about remote users and devices.
What the audit focuses on depends on the scope of the audit plan and the reason the audit was initiated.
What can you expect before, during and after software audits?
Before the audit
Before a software audit begins, the software vendor sends the organization a notice for audit. This letter should explain the audit and how the organization can help the process move smoothly. For example, the letter should include details such as what software is being requested for the audit, along with a time frame for the organization to respond to the audit request.
The organization should build a team of relevant employees to map out a strategy for the audit process, including roles, responsibilities and timelines. Employees from IT, legal and software procurement roles should be included in the team.
Team members from legal should review any possibly relevant information, such as the use of any end-user license agreement.
A role should also be established specifically for corresponding with the auditors. To keep third-party auditors from disclosing information to a software vendor, a nondisclosure agreement should be made among the third-party auditor, the organization under audit and the software vendor. The scope of the audit should be clearly defined, including the areas that are in the audit and the products used.
During the audit
At the start of a software audit, contracted auditors and the vendor meet with the organization to discuss each phase of the audit. This kickoff meeting should include subjects such as the timeline and scope.
The auditors begin collecting data important to the scope of the audit, such as hardware devices, lists of applications, the number of software licenses and proof of licenses. If a tool or script needs to be tested, the auditor should be made aware of the amount of time needed to do this.
After the audit
After the auditors perform the audit and recorders take notes on action items and recommendations, the auditors schedule a software audit review meeting with the organization being audited. This meeting discusses the audit report findings and addresses potential concerns. The auditors give the organization their findings so it can make improvements to those areas.
The organization can also hold a meeting with its contracted software vendors to negotiate how it can fix any mistakes.
Software audit checklist
Having a software audit checklist of steps to perform before the audit can help the process flow more smoothly. This list should include the following:

- Identify experts for audits. Picking candidates for a team to handle audits if and when they come up is a good idea to have ahead of time. These candidates can originate internally or externally and should be able to use their experience to create a smooth audit process.
- Prepare for the audit process. This list should include what policies and procedure documentation are in place; the hardware, software and licenses the organization uses; and proof of ownership.
- Conduct an audit review. A team of senior managers and external specialists should review the results of the software audit to determine the next steps.
- Use a software asset management tool. A SAM tool budgets software, enabling an organization to more easily find and correct license shortages and detect older, unused licenses.
Learn more about general compliance audit checklists, which can help ensure an enterprise is prepared for a compliance audit.
