robot
A robot is a type of automated machine that can execute specific tasks with little or no human intervention and with speed and precision. The field of robotics, which deals with robot design, engineering and operation, has advanced remarkably in the last 50 years.
IDC identifies robotics as one of six innovation accelerators driving digital transformation. The others include 3D printing, cognitive computing, next-generation security and virtual reality or augmented reality.
What can robots do?
Essentially, there are as many different types of robots as there are tasks for them to perform. Robots can perform some tasks better than humans, but others are best left to people and not machines.
The following are things robots do better than humans:
- Automate manual or repetitive activities in corporate or industrial settings.
- Work in unpredictable or hazardous environments to spot hazards like gas leaks.
- Process and deliver reports for enterprise security.
- Fill out pharmaceutical prescriptions and prep IVs.
- Deliver online orders, room service and even food packets during emergencies.
- Assist during surgeries.
- Robots can also make music, monitor shorelines for dangerous predators, help with search and rescue and even assist with food preparation.
Connected to the cloud
IDC predicted in its 2019 FutureScape report on robotics that of 40% of G2000 manufacturers will digitally connect (at least) around a third of their robots to cloud platforms to improve agility and operational efficiency by 2023. Furthermore, 25% of retailers will deploy robots to free workers from performing repetitive tasks.
Despite their increasing ubiquity, there are several shortcomings to using robots.
They can, for example:
- perform surgeries but not soothe scared patients;
- sense furtive footsteps in a closed-off area, but not take action against gate-crashers;
- lead exercise sessions for the elderly but not ease their loneliness;
- help medical professionals with diagnoses, but not empathize with patients; and
- learn from data, but not correctly respond to unexpected situations.
The increasingly complex capabilities of robots will eventually eliminate some human tasks, but not all. Current robotics technology can automate only 25% of tasks in unpredictable, human-dependent areas like construction and nursing. But robots depend on human programming -- and they (likely) always will.

Types of robots
There are as many different types of robots as there are tasks.
1. Androids
Androids are robots that resemble humans. They are often mobile, moving around on wheels or a track drive. According to the American Society of Mechanical Engineers, these humanoid robots are used in areas such as caregiving and personal assistance, search and rescue, space exploration and research, entertainment and education, public relations and healthcare, and manufacturing. As use cases and applications explode, the android market is poised to hit $13 billion by 2026.
2. Telechir
A telechir is a complex robot that is remotely controlled by a human operator for a telepresence system. It gives that individual the sense of being on location in a remote, dangerous or alien environment, and enables them to interact with it since the telechir continuously provides sensory feedback.
3. Telepresence robot
A telepresence robot simulates the experience -- and some capabilities -- of being physically present at a location. It combines remote monitoring and control via telemetry sent over radio, wires or optical fibers, and enables remote business consultations, healthcare, home monitoring, childcare and more.

4. Industrial robot
The IFR (International Federation of Robotics) defines an industrial robot as an "automatically controlled, reprogrammable multipurpose manipulator programmable in three or more axes." Users can adapt these robots to different applications as well. Combining these robots with AI has helped businesses move them beyond simple automation to higher-level and more complex tasks.
In 2019, there were over 390,000 industrial robots installed worldwide, according to the IFR -- with China, Japan and the U.S. leading the way.
In industrial settings, such robots can do the following:
- optimize process performance;
- automate production to increase productivity and efficiency;
- speed up product development;
- enhance safety; and
- lower costs.
5. Swarm robot
Swarm robots (aka insect robots) work in fleets ranging from a few to thousands, all under the supervision of a single controller. These robots are analogous to insect colonies, in that they exhibit simple behaviors individually, but demonstrate behaviors that are more sophisticated with an ability to carry out complex tasks in total.
6. Smart robot
This is the most advanced kind of robot. The smart robot has a built-in AI system that learns from its environment and experiences to build knowledge and enhance capabilities to continuously improve. A smart robot can collaborate with humans and help solve problems in areas like the following:
- agricultural labor shortages;
- food waste;
- study of marine ecosystems;
- product organization in warehouses; and
- clearing of debris from disaster zones.

Common characteristics of robots
Not all robots look like HAL 9000 in 2001: A Space Odyssey or BigDog -- a rough-terrain quadruped robot with complex sensors, gyroscopes and hydraulic actuators -- from Boston Dynamics. Some have human-like features (androids), while others are all mechanical limbs (PackBot). Still others look like keychains (Tamagotchi) or whizzing toys (Roomba).
Nonetheless, all robots have some common characteristics, such as the following:
- mechanical construction
- electrical components
- computer programming
As AI and software advance, robots will become smarter, more efficient and will take on more complex challenges.
Robotic process automation and intelligent process automation
Robotic process automation (RPA) technology involves the design, deployment and use of software-based robots to accomplish things like the following:
- automate rules-based business processes;
- streamline enterprise operations;
- save human effort; and
- lower costs.
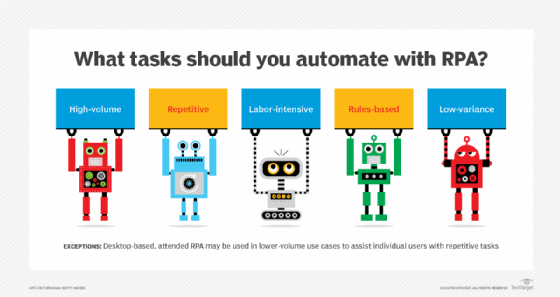
RPA automates repetitive tasks so human personnel can focus on more higher-value work. Use cases can be simple (automated email responses) or complex (automating thousands of jobs).
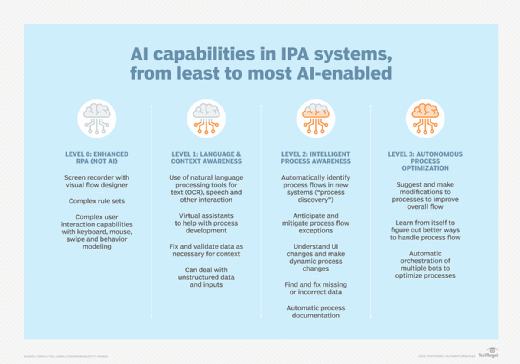
RPA is a steppingstone to more advanced intelligent process automation (IPA). IPA adds decision-making capabilities, AI tools and cognitive technologies like natural language processing and machine learning.
Robots and robotics: A short history
The 1921 play, R.U.R., which stands for Rossum's Universal Robots, by Czech writer Karel Capek, first introduced the word "robot." These robots were artificial people rather than machines, and could think for themselves, so they are somewhat similar to modern androids. Isaac Asimov said that Capek contributed the word robot to all languages in which science fiction is written. Asimov introduced the word robotics and his famous Three Laws of Robotics in his story "Runaround."
The first robots, although they weren't called that at the time, actually date back several centuries before the Roaring Twenties. In 1478, Leonardo da Vinci designed a self-propelled car -- still considered influential for robotic designs. While this autonomous system didn't make it past the drawing board, in 2004 a team of Italian scientists replicated its design as a digital model, proving that it works.
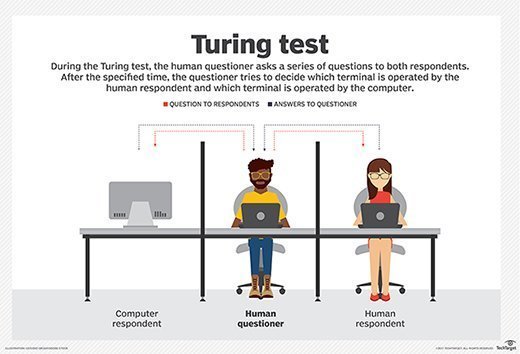
The path-breaking work of Asimov and da Vinci set the stage for the developments that followed. In 1950, English computer scientist Alan Turing developed the Turing Test -- originally called The Imitation Game -- laying the foundation for further research into artificial intelligence and robotics.
Stanley Kubrick's 2001: A Space Odyssey presented one of the world's earliest AI robots, the HAL 9000. HAL can recognize speech, understand natural language and even win chess games. Now a part of Carnegie Mellon University's Hall of Fame, HAL still inspires scientists to look for ways to duplicate its 1960s-imagined capabilities.
In the 1950s, George C. Devol invented a reprogrammable manipulator -- Unimate. Engineer Joseph Engleberger acquired Devol's robot patent and converted his design into the world's first industrial robot. He eventually earned the label: The Father of Robotics.
In 1966, MIT developed one of the earliest AI-based bots, ELIZA, while SRI International later designed Shakey, a self-directed robot, for specialized industrial applications. By the early 70s, scientists had successfully integrated bots into medicine with MYCIN to help identify bacteria and INTERNIST-1 computer-based diagnostic tool. In the 1980s, ALVINN, the robotics tech that powers today's self-driving cars was developed.
The Tramp foresees the robot's rise
"Don't give yourselves to these unnatural men -- machine men with machine minds and machine hearts! You are not machines, you are not cattle, you are men! You have the love of humanity in your hearts!"
-- Sir Charlie Chaplin, The Great Dictator
In 1940, Sir Charlie Chaplin probably had no idea that the inexorable rise of machines was just a few decades away. Over 80 years later, automated robots are now used in manufacturing, industrial supply chains, agriculture, financial services, education and more.
By the 1990s, consumer-facing bots appeared as computer games like Tamagotchi. Post 2000, interest in robots and robotics exploded with the release of SmarterChild, a programmed bot within AOL Instant Messenger that's now considered the forerunner AI to Apple's Siri.
In the early 2000s PackBot, a military robot, and Stanley, a vehicular bot, were both invented. Notably, PackBot played an important role in the aftermath of the 9/11 attacks, as first responders sent the robot into the rubble to search for victims and assess the structural integrity of the debris. PackBot sent back pictures from hard-to-reach places, helping with the rescue effort.

The PackBot inspired a new era of robotics, accelerating the development of more advanced, autonomous machines that now help in areas such as the following:
- disaster management
- law enforcement
- weather forecasts
- residential hygiene
- military reconnaissance
Later, household robots like Roomba and AI-based robots like Siri and Alexa paved the way for robots in people's everyday lives, furthering their potential.
Today's robots can carry out a number of complex tasks that would have been written off as science fiction even half a century ago. Smart, intelligent robots are now collaborating with humans and helping to solve problems that looked unsolvable in the past.
Also see: Nanotechnology, uncanny valley, telepresence robot and robotics






