third-party cookie
What is a third-party cookie?
A third-party cookie is a cookie that's placed on a user's device -- computer, cellphone or tablet -- by a website from a domain other than the one the user is visiting.
Third-party cookies are most frequently used for online advertising. These cookies track a user's browsing history and activities so they can present them with personalized ads for products and services. For example, if a user searches for party décor, their screen might pop up with party décor ads on multiple websites, especially social media websites such as Facebook. The user is now seeing these ads because their web browser stored a third-party cookie and is using this information to send them targeted ads.
However, third-party cookies are on their way out. With the exception of Google Chrome, browsers such as Apple Safari and Mozilla Firefox block third-party cookies by default. Google is expected to stop the use of third-party cookies by the end of 2024.
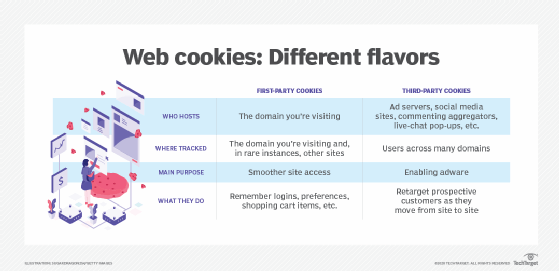
First-party cookies vs. third-party cookies
Both types of cookies are text files made up of bits of information that websites use to collect user data. Cookies typically store user data such as web surfing and personalization preferences and tracking information. The difference between the two types of cookies is who uses that cookie data and for whom the cookie collects data.
First-party cookies. The website owner places a first-party cookie on a website to collect user data they can use. First-party cookies are often used to improve user experience by remembering user preferences and settings. They're also used to store information, such as items a user has added to their online retail shopping cart, usernames, passwords and language preferences. Site owners can use first-party cookies to provide services such as live chat.
Third-party cookies. A third-party cookie is placed on a website by someone other than the owner -- a third party -- to collect user data for the third party. As with standard cookies, third-party cookies are placed so that a site can remember something about the user. Third-party cookies, however, are often set by advertising networks that a website might subscribe to in the hopes of driving up sales or page views. For example, if a user visits a website named news.com, a cookie placed on this domain by news.com is a first-party cookie. A cookie placed by any other site, such as an advertiser or social media site, is a third-party cookie.
In contrast to first-party cookies, which can only gather user data when users interact with the owner's website, third-party cookies track users across several websites, providing a more comprehensive picture of user behavior.
Cookies in general can also be referred to as Hypertext Transfer Protocol (HTTP) cookies, web cookies and browser cookies. Third-party cookies are also known as trackers.
How third-party cookies work
Third-party cookies embed JavaScript from one website into another website. A website hosts the third-party cookie by incorporating third-party JavaScript. HTTP, the protocol that's used for web browsing, is a stateless protocol, meaning information isn't saved in between browsing sessions. However, cookies remember stateful information -- or information that's saved between sessions -- in the stateless HTTP environment.
When creating a cookie, cookie attributes are specified in the HTTP response header that determines whether the cookie is a first or third party. The SameSite attribute lets the creator of the cookie determine whether the cookie becomes a third-party cookie or a first-party -- or same-site -- cookie. When a user makes a request to the browser or performs any action on the site, the cookie attributes determine if and when cookies are sent along with the response.
For example, if a website user requests an image from the same site domain, the cookie with the SameSite attribute records user information. If the user requests an image from a third-party site, where the domain name isn't the same, a cookie with the SameSite attribute won't collect user information across sites.
The SameSite attribute determines that the cookie will be first party. Within SameSite, there are a descriptors:
- If the cookie creator sets SameSite to "Strict," the cookie is strictly first party and won't ever be sent on cross-site requests. It's activated when the domain of both parties in the exchange come from the same web domain. This setting works well for remembering user preferences on the site but won't work for a request coming from an external link. For example, if the user clicks on a site link in an email from a friend, the cookie won't be sent because the user is coming from a different domain.
- If the cookie is set to "Lax," it will be sent on certain cross-site requests. Lax means the cookie is sent with secure, top-level navigation, which means the URL does change. Lax doesn't allow third-party sites to POST, or load, information on the original user site. This means that a third-party cookie set to Lax can be sent when a user clicks a link to the cookie's site but can't load advertisements from another site in an inline frame (iframe), for example, as this uses the HTTP command POST, which is considered less secure.
- If no specification is made, all requests are subject to cookies, and the cookie is by definition a third-party cookie. It doesn't restrict POST requests, which advertisers, social networks and other third parties can use to load information from their site. This lack of specification makes cookies useful for advertisers because they often use methods that don't fit the criteria of "SameSite = Strict" and "SameSite = Lax." For example, an external site makes a GET request that doesn't change the URL as a top-level navigation. This action -- which could be an <iframe> or <img> request -- is blocked by both Lax and Strict. Having no specification allows that type of communication, in which a page is loaded inside another page. This is a common way for advertisements to appear on web pages.
Why third-party cookies are used and who uses them
Third-party cookies get their name because they come from a website other than the one a user is currently on. Advertisers and social networks often use cookies to track users across domains and monitor their online activities. This is useful for advertisers because specific user data can enhance their success at target marketing.
Both advertisers and social media sites rely heavily on user data to inform the content they curate and generate. User profiles can be created from this data to inform how information is presented to the user, whether it's an advertisement pop-up or a social media feed.
How to tell when a website uses third-party cookies
To determine if a website is using third-party cookies, you can manually access the browser settings or use a free online cookie checker tool.
Instructions vary for different browsers Here's how to check for third-party cookies in Chrome.:
- Press Ctrl + Shift + I and choose Application > Storage > Cookies.
- Verify the domain of the cookie list. It's possible to tell if a website is using third-party cookies if the domain is different from the one being used or maintained at the moment.
Similarly for Firefox and Safari, open the developer console or inspect element and check for cookies.

Enabling, disabling and blocking cookies in Google Chrome
Third-party cookies are often blocked and deleted through browser settings and security settings such as the same-origin policy, which lets scripts contained in a first webpage access data in a second webpage as long as both webpages have the same origin. Browsers such as Firefox and Safari block third-party cookies by default.
Blocking third-party cookies doesn't create login issues on websites -- which can be an issue after blocking first-party cookies -- and could result in the user seeing fewer targeted ads on the internet. But blocking all cookies can sometimes lead to problems, as some websites rely on first-party cookies to function properly.
The following steps can enable or disable cookies in Google Chrome:
- Open Chrome.
- Click on the three dots in the upper right-hand corner of the browser window.
- Scroll down and click "Settings" and select the Privacy and Security section.
- Click on "Cookies and site data." The following options appear:
- Allow all cookies.
- Block third-party cookies in incognito.
- Block third-party cookies.
- Block all cookies.
- Click on the circle next to the option that most applies to you. Blocking all cookies is not recommended.
Third-party cookies and data privacy
Third-party cookies and cookies in general pose a significant data security risk and are viewed by some as infringing on user privacy rights. This is why several of the main browsers now block third-party cookies by default. In 2011, the European Union passed the cookie law that requires users to be informed of the cookies they'll be interacting with upon visiting a site.
Although not dangerous by themselves, malicious actors can hijack and use cookies to gain information. This happens when any cookie related to authentication isn't transmitted securely. For example, Kaspersky discovered a cookie-stealing Trojan that gives hackers the ability to control victims' social media accounts.
Cookies related to authentication normally have a security flag that instructs the browser to only access the cookie using secure channels such as Secure Sockets Layer or Transport Layer Security. If not transmitted using these channels, hackers can eavesdrop and gain access.
Other common attacks that use cookies in their method include the following:
- Cross-site request forgery.
- Cross-site scripting.
- Session hijacking.
What's happening to third-party cookies?
There has been a general move away from third-party cookies as consumers demand online privacy and have concerns about their personal data being mishandled by third parties. Millions of users are turning to ad blockers and private browsing, while privacy regulations are limiting the ability of companies to collect and use personal data, including the General Data Protection Regulation and California Consumer Privacy Act. Despite the fact that the birth of cookies three decades ago launched a $600 billion digital advertising industry, tech giants are now paying heed to consumers and have pledged to stop supporting them. While blocking third-party cookies increases user privacy and security, it does create problems for consumer tracking and ad serving firms, which often place ads that follow users around the web.
For marketers and advertisers, the eventual phase-out of third-party cookies doesn't come as a surprise. Google first revealed its intentions in February 2020 to gradually phase out third-party cookies on Chrome by 2022. Google later revised its plans to delay phasing out third-party cookies until 2024, primarily because it wanted advertisers to have more time to change their advertising tactics and test out new, less-intrusive targeted advertising technology. Once phased out, Google won't give users the option to turn third-party cookies back on.
What are some alternatives to third-party cookies?
According to recent Adobe research, 75% of marketing and customer experience leaders globally continue to rely heavily on third-party cookies. As it affects their survival, many web publishers have tried to undermine these changes by using other techniques such as cookie respawning, Flash cookies, entity tags and canvas fingerprinting.
The following are some alternatives to third-party cookies:
Browser fingerprinting. A browser fingerprint consists of a collection of details about the user, such as the type of browser they're using, the contents of their browser cache, their location and their time zone. It collects this information in a hash value, and the collector of the information can then look for that same combination of details and follow users around the web with accuracy.
Identity solutions. Identification options track users by using personal information, such as an email address, a phone number or a login ID. Personal information from website visitors is gathered and provided to an ID provider. The user's personal information is then encrypted or hashed to preserve their privacy before matching to an existing ID or creating a new ID. Because it can be used on various websites, channels and platforms, an ID formed with a persistent user identification, such as an email address, is referred to as a universal identifier.
Google topics. In 2019, Google launched the Privacy Sandbox, a search engine initiative to fulfill rising consumer expectations for more privacy. When it was first introduced, the Federated Learning of Cohorts (FLoC) was its focus. It was developed with the intention of creating groups of users with similar surfing preferences that could be shared with advertisers while preserving the user's anonymity. Nonetheless, methods of FLoC exploitation -- such as reverse engineering the algorithm -- have emerged, which could still let trackers create a unique digital fingerprint of the user. FLoC was finally transformed into Google Topics, which also uses the Chrome browser. Google Topics tracks a user's weekly usage to identify a select few topics that best reflect their top interests over the course of three weeks.
Contextual advertising. Internet advertisements that target users depending on the content of the website they're visiting are known as contextual advertising. Users don't need to give up any privacy because only ads that are pertinent to their interests are aimed at them. For instance, if a user was previously browsing a sports website and then clicked on a clothing website, they would only see sports-related advertisements on the sports page. This ensures that when users navigate between websites, their privacy is safeguarded.
Walled gardens. A walled garden is a closed environment where businesses are permitted to gather and use user data. Google, Facebook and Amazon are common examples. Businesses can keep a high level of confidence in the identification and conduct of users by managing the data that goes into and out of their ecosystem. Walled gardens are constructed based on logged-in users, letting them track each individual across devices. Walled gardens use a first-party platform, so third-party cookies aren't required.
Many marketing and sales operations depend on third-party cookies, whereas first-party cookies are used to gauge user engagement. Learn what makes the two cookies different from one another.
