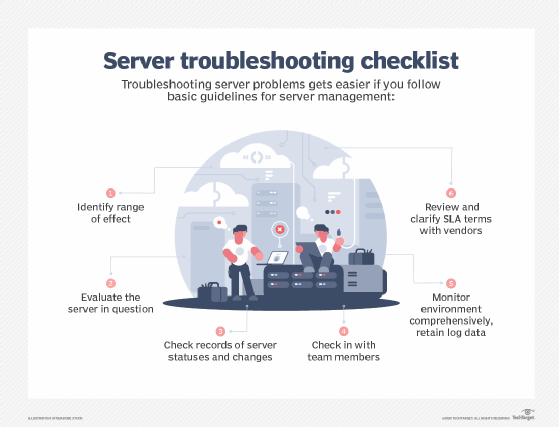
troubleshooting
What is troubleshooting?
Troubleshooting is a systematic approach to problem-solving that is often used to find and correct issues with complex machines, electronics, computers and software systems. The first step in most troubleshooting methods is gathering information on the issue, such as an undesired behavior or a lack of expected functionality.
Once the issue and how to reproduce it are understood, the next step is to eliminate unnecessary components to determine if the issue persists. This can help identify component incompatibility issues and problems caused by third-party products.
Troubleshooting methodologies usually try to isolate a problem so that it can be examined. The initial goal is to diagnose the problem and try obvious solutions, such as performing a system reboot, powering down and up, and checking that the power cord is connected.
Troubleshooters initially look for common, known causes. For example, when a laptop won't boot up, an obvious first step is to check whether the power cable is working. Once common issues are ruled out, troubleshooters must run through a checklist of components to identify where the failure is happening.
The primary objectives of troubleshooting are to figure out why something doesn't work as intended and provide a solution to resolve the issue.
How does troubleshooting work?
Computer problems that troubleshooters address can show up in any number of places. Examples of places troubleshooters find themselves working include the following:
- operating systems
- applications
- central processing units or CPUs
- firewalls
- hard drives
- solid-state drives
- servers
One basic troubleshooting method is to press Control-Alt-Delete on a PC, which opens the Microsoft Windows Task Manager where users can determine which applications have become unresponsive, close them and restart the computer. Similarly, Option-Command-Escape will force quit apps on a Mac.
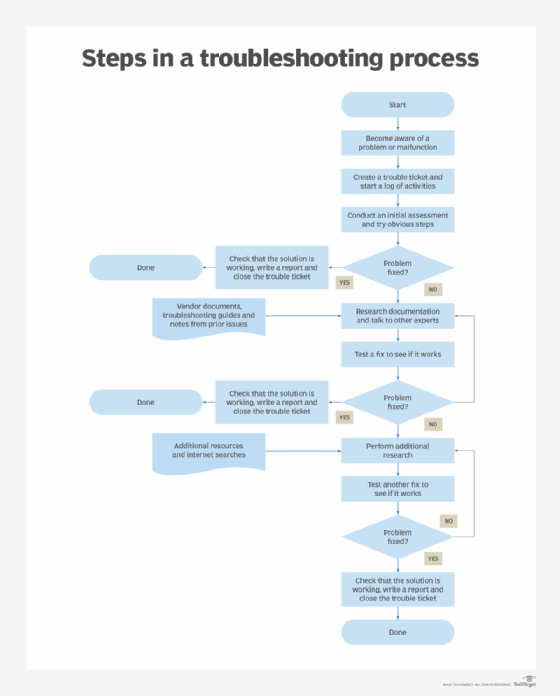
IT and help desk professionals use more extensive ways to troubleshoot problems. Troubleshooting methodologies vary, but the following seven steps are often used.
Step 1. Gather information
The first troubleshooting step for just about any problem is gathering information about it. This can be information about why something unexpected is happening or a missing capability.
Other important information includes related symptoms and unique circumstances that must happen to reproduce the issue. The goal is to identify the problem and understand how to reproduce it.
Step 2. Describe the problem
By comprehensively describing the issue, troubleshooters will know where to look for the root cause. It can help to ask the following questions:
- What are the symptoms?
- When does the problem occur?
- Where does the problem occur?
- What are the conditions when the problem occurs?
- Is the problem reproducible?
Answers to these questions will expose which components aren't part of the problem. They will also help identify possible compatibility issues among components and third-party products that might cause issues.
If the issue remains, a specialist might check other common causes, consult product documentation, and conduct research on a support database or through a search engine.
Step 3. Determine the most probable cause
Sometimes a problem can have many possible causes. A trial-and-error method is used to eliminate various options. The best approach is to look for the most straightforward cause first, even when working with a complex system.
One common testing method is the split-half troubleshooting approach. This technique isolates the source of a problem through a process of elimination. This method works best when the system involved has a number of parts in series. Troubleshooters first test halfway down the line of components. If the middle component works, they know everything before it works. At this point, they move on to the middle of the remaining untested section toward the end of the series. If the test of this second section works, they go on to the midpoint of the remaining section.
If the problem occurs at any point in this testing, then the troubleshooters do a split back toward the start of the series until the problem part is found. The split-half process can save time in systems that depend on many components.
Step 4. Create a plan of action and test a solution
Once the problem is understood, troubleshooters develop a plan to tackle the issue. They test their hypothesis and keep testing it until they identify a solution. When all tests fail, go back to Step 3 and start over.
Step 5. Implement the solution
Once troubleshooters have identified and understood the problem, they must adjust, repair or replace whatever is causing the issue. When that is done, they should test the solution to be sure the problem is fixed.
The goal is to return the system to the way it was before the problem occurred. Successful troubleshooting is indicated when the problem is no longer reproducible and functionality is restored. The success of the troubleshooting process often depends on the technicians' thoroughness and experience.
Step 6. Analyze the results
Sometimes the solution to a problem creates another issue. Troubleshooters must monitor the system to ensure the changes made don't adversely affect other parts of it or other systems connected to it.
Step 7. Document the process
The final step is to document all steps taken. This ensures other troubleshooters will know what to do if the problem happens again. It's critical to document both the solution and the fixes that didn't work to provide a comprehensive record of the incident. Documentation will also help in creating troubleshooting checklists to quickly identify and fix potential problems.
Other troubleshooting resources
Troubleshooting is an iterative, trial-and-error process that is repeated until the issue is fixed. The following are some additional steps to consider for effective troubleshooting:
- The device manufacturer's technical manual is a good source of troubleshooting tips.
- Troubleshooting guides might also be available.
- Other subject matter experts can have helpful ideas.
- An online search can often identify solutions to common problems.
- In a complex malfunction that appears to affect multiple components, it might be necessary to identify the root cause of the problem before fixing individual issues.
- It might be necessary to work with a specialist with forensics expertise as part of the diagnostic process.
When troubleshooting a wireless network, check out these 10 possible problem areas.