tuple
What is a tuple?
A tuple, pronounced TUH-pul, is an ordered and finite list of elements in various fields of interest, including computing. The exact nature of that list depends on the context in which it is used, although the meaning is conceptually similar across disciplines. Tuples are found in mathematics, computer programming and the relational data model on which many modern database systems are based.
Tuples in mathematics
In mathematics, a tuple is an ordered sequence of values. The values can be repeated, but their number is always finite. A tuple is often represented by a comma-delimited list whose values are enclosed in parentheses, although they're sometimes enclosed in square brackets or angle brackets. The following tuple uses parentheses and contains four values, with one value repeated.
(6, 12, 6, 4)
Because the tuple includes four values, it is sometimes referred to as a 4-tuple or a quadruple. Tuples are often referred to by these types of specific names, particularly the ones with fewer values. For example, tuples that contain one through six values might be referred to by the following names:
- 1-tuple or monad.
- 2-tuple or pair.
- 3-tuple or triple.
- 4-tuple or quadruple.
- 5-tuple or quintuple.
- 6-tuple or sextuple.
These are not the only names given to tuples that contain one to six values. In addition, names are often given to tuples that contain more than six values. A tuple might also be referred to as an n-tuple, where n is the potential number of values within the tuple. An n-tuple can be represented by the following expression.
(x1, ..., xn)
A tuple is considered ordered because that order uniquely defines the tuple, in terms of comparing it with other tuples. For example, the following statement is true only if a1 equals b1, a2 equals b2, a3 equals b3 and so on.
(a1, a2, a3, ..., an) = (b1, b2, b3, ..., bn)
If the individual values are not equal according to the specified order, the statement is false. If a1 equals b2 and a2 equals b1, but a1 does not equal b1 and a2 does not equal b2, the statement is false.
Tuples can be used together as part of larger calculations. A simple example of this is shown in the following equation, which adds two 4-tuples together.
(3, 1, 17, 7)
+ (6, 12, 6, 4)
= (3 + 6, 1 + 12, 17 + 6, 7 + 4)
= (9, 13, 23, 11)
The values are added together based on their position within the tuple, with each position being calculated together but independently of the values in the other positions. The first value in the first tuple is 3, and the first value in the second tuple is 6. When added together, they total 9, which becomes the first value in the tuple returned by the calculation. The same process is repeated for each position within the tuple.
In mathematics, a tuple might also be represented in a column format rather than as a single row of elements. When a column format is used, the values are enclosed in brackets, without commas, as in the following example.

Tuples in this format can also be added together, taking a similar approach as in the earlier example.
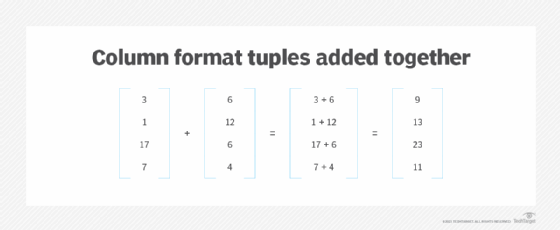
The values are added together based on their position within the tuples. Because each tuple has four values, the equation returns a 4-tuple with the sum of each position.
Tuples can be used in a variety of ways in mathematics. For example, they might be used to track a list of values, such as all the prime numbers between 1 and 100. They might also be used for vectors in two-dimensional and three-dimensional space or in calculations that involve sets and functions.
Tuples in computer programming
Some programming languages include a data element referred to as a tuple, which is similar in concept to the tuple used in mathematics. Tuples in programming are also ordered lists with a finite number of elements. In addition, the tuple's values can usually be duplicated and be of any type. A tuple's elements are also typically immutable -- something that cannot be changed. This immutability often translates to better performance than a data structure such as an array or list, whose values can be changed.
Python, Swift, C# and Visual Basic are all examples of programming languages that support tuples. Some languages, such as Java, do not support tuples inherently, but support can be added by importing a special library.
The ways in which tuples are defined and accessed are specific to each programming language. In Python, an object-oriented language, for example, the process of creating a tuple is very straightforward.
tuple1 = ('book', 47.932, 1872, 'elevate', 0);
In this case, the tuple is named tuple1 and contains five elements, which are a mix of string, integer and float values. The values within a tuple can be accessed in their entirety or by individual elements. The following print statement returns all the elements in the tuple.
print(tuple1);
The statement gives us the following results, which reflect exactly how the tuple was defined.
('book', 47.932, 1872, 'elevate', 0)
You can also access individual values within a tuple.
print(tuple1[0]);
The statement retrieves the tuple's first value, book. As with many data structures in programming, Python tuples use 0-based indexing, so you must start with 0 when referencing individual elements within a tuple. This indexing is also a factor when you want to access a range of values within a tuple.
print(tuple1[1:3]);
This time, the statement returns the second and third values, 47.932 and 1872, although not the fourth value, as might be expected.
In addition to the indexes, Python also includes several functions for working with tuples. For example, you can use the len function to retrieve the number of elements in a tuple, which in this case is 5.
print(len(tuple1));
Python also includes the tuple method for explicitly creating a tuple.
tuple2 = tuple(0.11, 88, 'test', 'test', -477.62);
It is also possible to create an empty tuple in Python. For this, you simply pass in a set of empty parentheses.
tuple3 = ();
To create a tuple with only one value, you must include a trailing comma to prevent Python from creating a string object instead of a tuple.
tuple4 = ('single',);
Python also lets you embed a tuple or other type of data structure within a tuple, as in the following example, which includes a tuple as the third value.
tuple5 = ('carry', 192, (-89.73773, 18, 'distinct'));
Python is, of course, only one programming language. The rules that govern tuples are specific to the language in which they're created. In C#, for example, you can create a tuple by using the Tuple class constructor or the Create method within that class. The Swift language is a little different from either Python or C#. With Swift, you can create a tuple similar to how it's done in Python, but Swift also supports other features, such as the ability to name elements within a tuple.
Tuples in the relational data model
Tuples are an integral part of the relational data model, which was first proposed by Edgar F. Codd in the 1970s. The model describes how to represent data in a way that ensures the data's integrity at all times, regardless of the supported workloads and applications.
Since its introduction, Codd's theoretical model has become the de facto standard for how mission-critical data is stored and protected, providing the foundation for database products such as SQL Server, Oracle Database, MySQL and numerous other relational database management systems (RDBMSes).
At the heart of the relational model is a gridlike structure that provides a framework for how to store and protect data. Data that is related in a meaningful way is organized into structures known as relations, which are physically implemented in a database as tables. For example, a retail store might design a database that includes one relation for employees, one for customers and one for products.
The relation's structure is defined by a set of attributes that organize the relation's data into specific categories and types. For instance, the employee relation might include attributes for an employee's ID, name, network login and other information. The physical counterparts for attributes are columns or fields.
The data in a relation is also organized by tuples, which group corresponding data into related sets. For example, the employee relation would likely include a tuple for each employee, and each tuple would include a value for each attribute. In a physical database, tuples are referred to as rows or records. The following image shows an example of what the employee relation might look like in the relational data model.
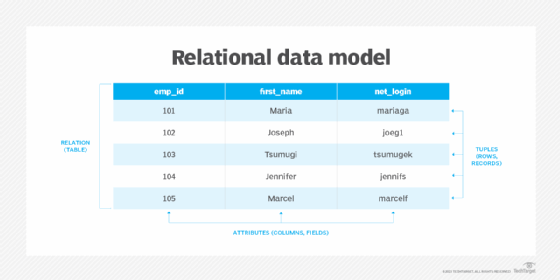
A relation can contain zero or more tuples, just like a table in a physical database can contain zero or more rows. Each tuple must include exactly the same number of values, and those values must correspond and conform to the defined attributes. If a value is missing, the RDBMS must be able to accommodate for its absence. For example, a default value might be assigned to a specific attribute, or the attribute might support null values or empty strings. In this way, the relation's underlying structure of attributes and tuples remains uncompromised.
Compare database management system vs. relational database management system.
