default password
What is a default password?
A default password is a standard preconfigured password for a device or software. Such passwords are the default configuration for many devices and, if unchanged, present a serious security risk.
Default passwords are intended to be placeholders and used only for the initial setup of hardware or after a factory reset. The user enters the password and is usually prompted to change it as part of the process, but not always.
Examples of default passwords include admin, password and guest. When vendors use these single default passwords, they can be easily found online through search or on websites that provide compiled lists. This makes them a large security risk if left unchanged.
What are default passwords used for?
Default passwords are commonly used for routers, access points, switches and firewalls. They're also common in embedded systems, industrial control systems (ICS) and remote terminal interfaces.
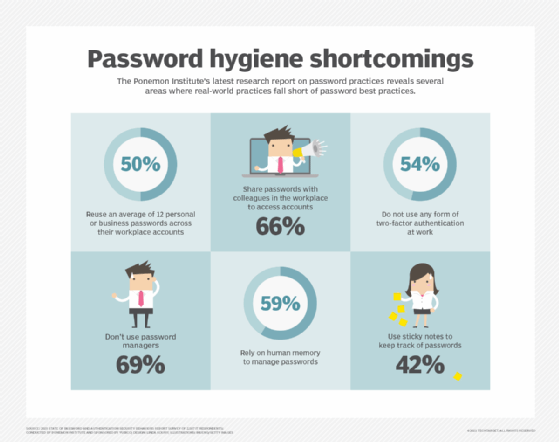
Why are default passwords a security risk?
Left unchanged, default passwords provide an easy attack vector for network equipment; if the owner also connects to a corporate network, that risk extends to the business as well. An attacker who logs into a device successfully is likely to have administrative-level access. This gives them complete control over the device and any connected networks.
The risk is also severe with embedded systems and ICS security because these environments weren't originally intended to be accessible over the internet. However, given today's IoT environments, almost anything can be made available via an internet connection, and while there are many benefits to IoT connectivity, enhanced security isn't among them.
How can default passwords be mitigated?
Default passwords are a well-known security risk that can easily be mitigated by changing them to strong, unique ones.
This should be done for every device on a network, including routers, switches and access points. For more sensitive devices, such as those used in ICS security or supervisory control and data acquisition (SCADA), it's also important to change the default username.
What are the characteristics of a strong password?
The following are some characteristics of a strong password:
- at least 8 characters long;
- a mix of upper and lowercase letters, numbers and symbols;
- not a dictionary word or a word that's easily guessed;
- changed regularly; and
- not reused on other accounts.

How should passwords be stored?
Passwords should be stored in a password manager. This is a piece of software that stores passwords securely, encrypting them so that they can only be accessed with a master password. A password manager can generate strong passwords and help manage different ones for various accounts.
When choosing a password manager, look for one that offers two-factor authentication (2FA) or multi-factor authentication (MFA).
As mentioned above, this adds an extra layer of security by requiring the user to confirm their identity with a second factor, such as a fingerprint, PIN or one-time code sent to their phone.
Learn how to prevent password attacks and other unauthorized threats, discover the top cybersecurity best practices to protect your business and explore five important password hygiene tips and best practices.
