volt per meter (V/m)
What is volt per meter (V/m)?
Volt per meter is the standard unit of electric field (E field) strength. Symbolically, it is represented as V/m. An E field of 1 V/m refers to a potential difference of 1 V between two points 1 m apart.
In base Standard International (SI) units, 1 V/m is the equivalent of 1 meter per kilogram per second cubed per ampere. This is represented as m . kg . s -3 . A -1.
Volt per meter explained
When electricity flows through an electrical conductor, it produces an electromagnetic field (EM field or EMF). This EMF contains both a magnetic (M) and electric (E) component. Volt per meter indicates the strength or intensity of the E field in the EM field. Simply put, if 1 V is applied between two infinite parallel planes spaced 1 m apart, the electric field strength is 1 volt per meter.
Example
Consider a parallel plate capacitor.
Situation 1
Suppose 1.5 V are applied across the capacitor whose plates are 1.5 m apart. The E field strength can be expressed in terms of V/m as the following:
E field = 1.5 V / 1.5 m = 1 V/m
Situation 2
Now, if the plates are moved toward each other so that the distance between them is 1 millimeter, the E field changes to the following:
E field = 1.5 V / 0.001 m = 1,500 V/m
Situation 3
The distance between the plates remains 1.5 m. However, a higher voltage (say 3 volts) is applied between them. The E field can now be measured as the following:
E field = 3 V / 1.5 m = 2 V/m
This example shows that volt per meter is affected by both the distance between the conductor's plates and the voltage applied between them.
The higher the source voltage, the higher the strength of the E field. This strength also decreases as the distance from the source increases and if there are shields, such as walls, houses or trees, in place.
Volt per meter is a vector quantity since it is characterized by both magnitude and direction.
Fractional and multiple values of volt per meter
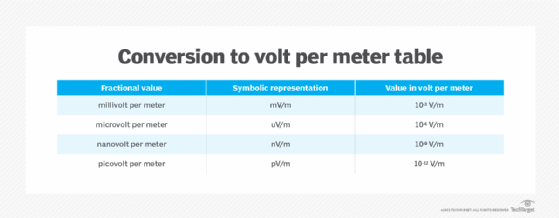
In a distant radio transmitter, the magnitude of the E field is often much less than 1 V/m. In such cases, fractional units are preferred to represent it. The most commonly used fractional units are as follows:
- Millivolt per meter
- Microvolt per meter
- Nanovolt per meter
- Picovolt per meter
Figure 1 shows how these values convert to volt per meter.
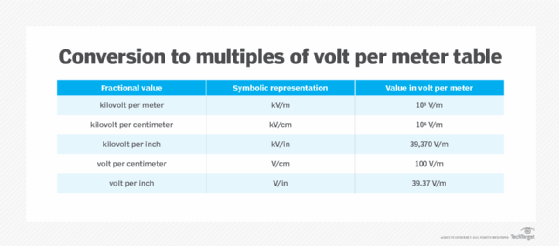
Multiples of volt per meter are represented as shown in Figure 2.
Volt per meter versus power in watts
The electric field created by the operation of a transmitter is usually represented in mV/m or uV/m. A watt is the unit that describes the amount of power generated by the transmitter.
A transmitter that generates constant power can produce E fields of different strengths, depending on the type of transmission line and antenna connected to it. In general, power and E field are related by the following formula:
(P. G) /(4 . π . d2) = (E2) / 120
The following explains the variables in the formula:
- P = transmitter power (watts)
- G = numerical gain of the transmitting antenna (for a unity gain antenna, G = 1)
- d = distance of the measuring point from the electrical center of the antenna (meters)
- E = field strength (V/m)
- 4 . π . d2 = surface area of the sphere centered at the radiating source
The E field causes interference in radio communications. Also, it does not directly correspond to the level of transmitter power. This is why the emission limits of broadcasting transmitters and short-range devices are specified in field strength.
Volt per meter and newton per coulomb
A newton per coulomb (N/C) is also a unit of the strength of the electric field in the SI system. An E field of 1 N/C is created if 1 V is applied between two infinite parallel planes spaced 1 m apart.
Mathematically, the electric field can be represented as the following:
E = F/Q
The variables in this formula are as follows:
Q = charge present in space
F = force exerted by Q on any other charge in its vicinity
The SI unit of F is 1 Newton (N) and the unit of C is 1 coulomb (C).
So, E = 1 N/1C = NC-1.
At the same time, when a new charge q is in the vicinity of charge Q, a force of repulsion acts on q. This charge can be moved through a distance in the field by applying some work (W) on it. The work done per unit charge is the electric potential, which is represented as the following:
V = W/q
But also:
work = force x displacement = F . d
Therefore:
V = F . d/q = E . d = V/d
In SI units, the unit of electric potential is volt (V) and the unit of displacement is meter (m). Therefore, the unit of electric field is as follows:
E = (1 V)/(1 m) = V/m
From the above, we can see that 1 V/m is equivalent to 1 N/C. This is why both volts per meter and newtons per coulomb are used to represent the strength of an electric field.
See also: Table of Physical Units
