Top 8 in-demand cybersecurity jobs for 2024 and beyond
Cybersecurity is a challenging career path, filled with professional opportunities. Learn about the top cybersecurity jobs and the training and background they require.
Organizations have their work cut out for them cybersecurity-wise, which is why they need competent cybersecurity professionals who can bring the right balance of skills, knowledge, best practices and experience to protect the company. The "2023 Cybersecurity Skills Gap" report from Fortinet found that 56% of firms struggle to recruit cybersecurity talent while 54% find it hard to retain them, putting many organizations at risk.
This problem represents a world of opportunities for skilled cybersecurity professionals. With 83% of company boards recommending a higher security headcount, according to the Fortinet report, the demand for trained, certified and skilled cybersecurity professionals is at an all-time high -- particularly for the eight specialists described below.
Who are these specialists? What are their skill sets? What does a career in cybersecurity look like for each of them? What's the role type? And what's the average salary for each role?
Read on to learn about the most in-demand cybersecurity jobs.
1. Cybersecurity engineer
Role level: Advanced/experienced
Role type: Technical
Average salary: $101,584
A cybersecurity engineer builds information security (infosec) systems and IT architectures and protects them from unauthorized access and cyber attacks. Cybersecurity engineers develop and enforce security plans, standards, protocols and best practices, and they build emergency plans to get things up and running quickly in case of a disaster.
Proactive thinking, planning and action are critical to this role. Cybersecurity engineers often spend a lot of time finding system vulnerabilities through penetration testing and figuring out how to deal with them before they become serious security issues. They might also review the organization's legal, technical and regulatory areas that affect IT security and recommend modifications for the same.
Other duties include the following:
- Creating and installing firewalls and intrusion detection systems.
- Updating security software, hardware and facilities, or evaluating new ones for implementation.
- Running encryption programs.
In addition, a cybersecurity engineer's job includes dealing with a detected security issue by moving data or information, or by working with outside teams to help the organization recover from a data breach.
People in this role must have strong communication skills to explain complex issues to management and to lay out the best ways to implement the latest security plans and procedures. They might also have to work with law enforcement following an attack.
Education and skills
- Bachelor's degree or higher: computer engineering, cybersecurity, infosec or a related field.
- Secure coding practices and vulnerability detection.
- Risk assessment.
- Secure network design and architecture.
- Firewall architecture.
- Computer forensics.
- Identity and access management.
- Virtualization technologies.
- Defending against advanced persistent threats, malware, phishing and social engineering.
- Encryption technologies.
Certifications
- CompTIA Cybersecurity Analyst (CySA+).
- CompTIA Advanced Security Practitioner (CASP+).
- Cisco Certified Network Professional Security (CCNP).
- Certified Information Systems Security Professional (CISSP).
2. Infosec analyst/cybersecurity analyst
Role level: Entry-level/midlevel/experienced
Role type: Technical
Average salary: $80,967
A security analyst's role is fairly broad and can encompass numerous responsibilities, such as monitoring security best practices, protocols and procedures with the right tools and ensuring practices are properly implemented and followed. People in this role analyze reports from these tools to proactively identify unusual or anomalous network behaviors. They might also control file access and credentialing, network updates and firewall maintenance.
A well-trained security analyst will have a solid understanding of how data is stored and managed, and the different kinds of cybersecurity threats, including ransomware attacks, social engineering and data theft. They might perform penetration testing and vulnerability scans and recommend relevant changes to improve security.
At large companies, security analysts might work in a security operations center to specifically monitor, detect, contain and remediate threats. At midsize and smaller organizations, security analysts might play a broad role, handling everything from security analysis and intrusion detection to firewall maintenance, antivirus updates and patch updates. Since they have expertise in security risks and best practices, they might be asked to train employees on cybersecurity hygiene.
Education and skills
- Bachelor's degree: computer science, cybersecurity, infosec or a related field.
- Proprietary network management.
- Penetration testing.
- Security incident triaging.
- Risk assessments.
- Data encryption.
- Firewall design, configuration, deployment and maintenance.
Certifications
- CompTIA Network+.
- CompTIA Security+.
- CompTIA PenTest+.
- CySA+.
- CISSP.
3. Network security architect
Role level: Advanced/experienced
Role type: Technical and managerial
Average salary: $126,166
A network security architect plays a critical role in improving the security strength of enterprise architecture, while maintaining network productivity, efficiency, availability and performance. Network security architects help translate business needs into functional systems, define appropriate policies and procedures for those systems and even help train users and administrators. They also keep an eye on budgetary and operational constraints. This is why people and managerial skills are important to have in this role.
To ensure ongoing security throughout the network lifecycle, network security architects undertake defensive measures, such as firewall and antivirus configuration, and offensive measures, such as penetration testing. They also oversee network changes to ensure minimal risk to the organization. They're expected to have advanced knowledge of different security tools and techniques related to firewalls, penetration testing and incident response. They must also be aware of computer systems' networking requirements, including routing, switching and trust domains, as well as security best practices, technologies and industry-standard frameworks.
They conduct network and systems analyses to identify and select the best control mechanisms for the required security level. They must be aware of various access control mechanisms, including role-based access control, mandatory access control and discretionary access control.
Education and skills
- Required: Bachelor's degree in computer science or a related field.
- Preferred: Master's degree in cybersecurity.
- Strategic planning.
- ITIL and COBIT IT process models.
- Knowledge of TCP/IP networking and networking security.
- Open Systems Interconnection 7-layer model.
- Intrusion detection systems.
- Risk management.
- Single sign-on identity management systems.
- VPN layers and connections.
- Protocol encryption.
Certifications
- CompTIA Network+.
- ISC2 Information Systems Security Architecture Professional.
- GIAC Defensible Security Architecture.
- NSE 7 Network Security Architect.
- Fortinet Network Security Expert (NSE).
4. Security software developer
Role level: Midlevel/senior/lead
Role type: Technical
Average salary: $75,776
A security software developer's role is perfect for someone who wants to write software code and is also interested in infosec. By combining technical programming knowledge with product development and security analysis skills, a security software developer creates software and adds security to it to "harden" it from potential attack. To do this, they must have up-to-date knowledge of the threat landscape, which is why entry-level roles in this area are virtually nonexistent.
A security software developer should be able to conceptualize tomorrow's threats today and take action to address those threats early. They should also balance product speed, functionality, user experience and security, so there are no unnecessary tradeoffs or costly errors. Security software developers will typically work with other professionals -- such as designers, engineers and testers -- so, in addition to technical knowledge of software architecture, design and coding, they should have strong communication and collaboration skills.
In general, security software developers are in great demand and have plenty of opportunities in IoT and other emerging areas of technology.
Education and skills
The following encompass the education and skills generally desired for midlevel roles:
- Bachelor's degree in software development or software engineering.
- Secure coding practices.
- Security controls.
- Penetration testing, which is preferred but not always required.
Those seeking advanced roles generally need the education and skills listed above, plus the following:
- Infosec.
- Cryptography.
- Project management.
- Network security.
Certifications
- CompTIA Security+.
- CySA+.
- CompTIA PenTest+.
- CASP+.
- Certified Information Systems Auditor.
- CISSP.
- Certified Information Security Manager.
- Cisco Certified Internetwork Expert.
- Microsoft Azure Security Engineer Associate.
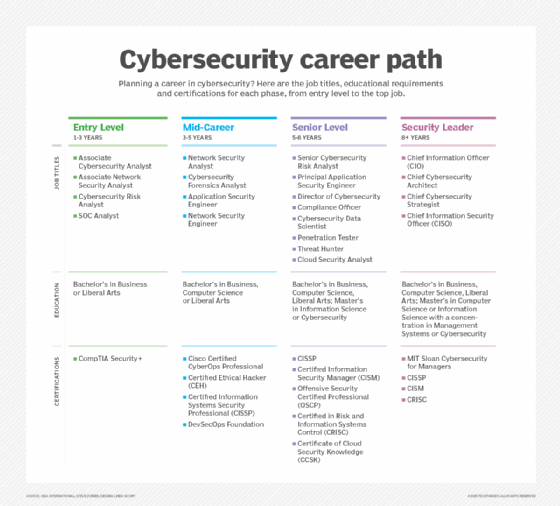
5. Penetration tester/ethical hacker
Role level: Junior/associate/midlevel/senior/lead
Role type: Technical and reporting
Average salary: $92,759
Ethical hackers are the private eyes of the cybersecurity world: They act like the bad guys to understand the attackers' motives, approaches and threat actions. They conduct penetration testing to find vulnerabilities and gaps in security protocols for networks, OSes, devices and web-based applications. They also suggest relevant fixes before these vulnerabilities can be exploited by bad actors. They play a proactive role in safeguarding the organization's information and systems.
Since they often work on highly confidential and time-sensitive projects, ethical hackers should be trustworthy and able to tolerate high levels of stress and uncertainty. They should also be creative and highly organized to effectively record and track their projects. Most importantly, they must constantly update their knowledge, skills and techniques to preempt cybercriminals' activities, and assist in incident handling and forensic analysis to improve the organization's security posture.
Some organizations differentiate between pen testers and ethical hackers. In these firms, pen testing is one of the functions of an ethical hacker who also has strong tactical cyber skills plus deep knowledge of the organization's vulnerabilities and vulnerability management approach. In others, the two roles are considered interchangeable.
Education and skills
- Bachelor's degree: infosec or a related field.
- Penetration testing methods and tools -- e.g., Network Mapper, Wireshark and Kali.
- Knowledge of Python, Golang, Bash and PowerShell.
- OWASP Top 10 vulnerabilities.
- Social engineering.
Certifications
- PEN-200 Offensive Security Certified Professional.
- GIAC Penetration Tester.
- GIAC Certified Enterprise Defender.
- GIAC Exploit Researcher and Advanced Penetration Tester.
- CompTIA Security+.
- CySA+.
- CompTIA PenTest+.
6. Application security engineer
Role level: Junior/midlevel
Role type: Technical and communication
Average salary: $137,404
In the software development lifecycles (SDLCs) of the past, security was viewed as something that could be reviewed and then simply tacked on to the finished software product once development was complete. But as we have seen, organizations are increasingly vulnerable to cyber attacks and data breaches. To stay safe from such serious threats, organizations need to ensure that security is not tacked on but baked into software applications. And this is primarily the responsibility of an application security engineer.
This specialist ensures developers follow secure coding practices at every step of the SDLC. They also help the development team test the application against specific security risks and parameters prior to its release.
The application security engineer is responsible for engineering the software in a secure manner. And for this, they must be able to do the following:
- Understand development environments -- many application security engineers are former coders and programmers.
- Understand how code is written and how the software is built.
- Perform code reviews, application vulnerability scanning and pen testing.
- Prioritize vulnerabilities and help developers to assess and remediate them.
- Understand how the application will run in the production environment and how it could be vulnerable in the real world.
- Maintain technical documentation.
An application security engineer plays a vital role in improving application security and ensuring the final product can successfully operate in the current threat landscape. Ideally, this person should have coding experience. However, they can do their job even if they lack this experience, provided they can effectively communicate with the dev team and other teams in the product engineering pipeline and explain any security issues in the context of the application's code.
Education and skills
- Bachelor's degree: computer science or a related field.
- Knowledge of encryption techniques in databases and the cloud.
- Working knowledge of software development, network engineering, security protocols, systems engineering, web application security and cryptography (preferred).
- Clear conceptual understanding of the SDLC.
- Familiarity with secure coding best practices.
- Knowledge of existing and emerging security threats.
- Robust communication and soft skills.
Certifications
- Certified Secure Software Lifecycle Professional.
- CISSP.
- MCSI-Certified Application Security Engineer.
- Certified Application Security Engineer.
More on building a cybersecurity career
Enhancing your cybersecurity knowhow is a great way to start moving into a job on a security team. Check out these resources for some initial steps to take:
7. Malware analyst
Role level: Midlevel/experienced
Role type: Technical, plus reporting and communication
Average salary: $155,000
Education and government were the favorite targets of ransomware attackers, experiencing an increase in such attacks by 411% and 887%, respectively, according to the "2023 SonicWall Cyber Threat Report."
Malware types and capabilities are constantly evolving, which explains why more organizations are falling victim to this threat. Worse, many companies are struggling to keep up with new and emerging forms of malware that spread quickly and are difficult to detect. This is why the demand for malware analysts is surging like never before.
A malware analyst identifies and examines malware-related threats. They also analyze malware-related incidents that have already happened. Their goal is to understand the nature of such threats and attacks to do the following:
- Reverse engineer malicious code.
- Understand how an attack was deployed and why it was successful or not.
- Develop and refine malware protection tools.
- Document suitable methods to avoid malware threats in the future.
Since malware analysts must understand code as well as threats, they're required to combine the skills of both security engineers and programmers. Many malware analysts first gain several years of experience in programming and software development before they step into this niche role.
A competent malware analyst must also have strong digital forensics skills, know how to use debugger tools like OllyDbg and dev environments like IDA Pro and be aware of cutting-edge attack techniques and anti-attack methods. It's unlikely a recent graduate would have all these skills and capabilities, which is why most malware analysts are mid-senior-level cybersecurity professionals.
Education and skills
- Bachelor's degree: computer science, cybersecurity or a related field.
- Experience with programming: C/C++ preferred since many malware strains are written in these languages.
- Ability to write scripts in Python, Perl and Ruby.
- Strong knowledge of tools such as IDA Pro, OllyDbg, RegShot, WinDbg, Immunity Debugger and TCP view.
- Working knowledge of Windows API and Windows OS internals.
- Ability to reconstruct unknown TCP/IP protocols, file formats and data structures.
- Ability to write technical reports and to communicate with dev teams and senior leadership.
Certifications
- GIAC Reverse Engineering Malware.
- CISSP.
- Certified Ethical Hacker.
- Certified Malware Analysis Professional.
- Certified Reverse Engineering Analyst.
8. Computer forensics analyst/digital forensics examiner
Role level: Entry-level/midlevel/senior
Role type: Technical, reporting and communication
Average salary: $76,289
A computer forensics analyst -- also known as a digital forensics examiner, forensic technician or cyberforensic analyst -- is the crime scene investigator of the cybercrime world. This specialist is of immense value when it comes to investigating cybercrimes that have affected an organization and figuring out how to prevent them from happening again.
Through their investigations, computer forensics analysts discover how a threat actor gained access to the enterprise network and what security gaps must be plugged to prevent the recurrence of such unauthorized access events. They also analyze digital evidence left behind by the attacker, prepare evidence for legal or law enforcement purposes and, when required, provide expert testimony during court proceedings.
Other crucial tasks performed by a computer forensics analyst include the following:
- Analyzing log files to determine the perpetrator(s) of a network intrusion or attack.
- Performing file signature analysis and file system forensic analysis.
- Gathering and analyzing intrusion artifacts, such as source code, malware or system configuration details.
- Working with the security team to mitigate future cybersecurity incidents.
This is a critical role in cybersecurity teams. Moreover, it requires a knowledge of cybersecurity from a technical, criminal and legal perspective, which fresh graduates typically can't yet bring to the table. Therefore, most digital forensics roles are in the mid-senior career range. However, some companies in the private sector, as well as some local, state and federal government agencies, do hire forensics analysts at the entry level, provided the candidate can show they have the required knowledge and skills.
Education and skills
- Bachelor's degree in computer forensics or similar area.
- Knowledge of anti-forensics tactics, techniques and procedures (TTPs).
- Knowledge of data carving tools and techniques, malware analysis tools and binary analysis.
- Knowledge of and experience with forensic tool suites, analyzing anomalous code, analyzing volatile data, processing digital evidence and preserving evidence integrity.
- Ability to interpret tool results to ascertain TTPs.
- Ability to conduct bit-level analysis and analyze memory dumps to extract information.
- Ability to identify obfuscation techniques.
- An understanding of law and criminal investigation techniques.
- Strong analytical and communication skills plus attention to detail.
Certifications
- Certified Forensic Computer Examiner.
- Certified Computer Examiner.
- GIAC Certified Forensic Examiner.
- GIAC Certified Forensic Analyst.
- EnCase Certified Examiner for forensic examiners using Opentext EnCase Forensic.
Wrap-up
As the number, scope and scale of cyber attacks increases, the demand for qualified cybersecurity professionals is also on an upswing. Not only is the field interesting and fulfilling, it offers numerous opportunities for career growth, high rewards and the chance to make a real difference to organizations and industry.
Rahul Awati is a PMP-certified project manager with IT infrastructure experience spanning storage, compute and enterprise networking.







