MP3 (MPEG-1 Audio Layer 3)
What is MP3 (MPEG-1 Audio Layer 3)?
MP3 (MPEG-1 Audio Layer 3) is a method to compress and store audio. An MP3 file can compress a music file by up to 95% of its original CD-quality size while maintaining good enough audio quality.
How does MP3 work?
Computers are digital devices, representing data as discrete numbers, while sound is analog, which can exist at any value. For a computer or any digital device to store sound, it must encode the audio waveform as a series of numbers. This encoding is typically done using 16 bits sampled at 44.1 kilohertz for CD audio. This represents a lot of data -- about 10 megabytes (MB) per minute. This is known as CD-quality or uncompressed audio and is often stored as a WAV file on a computer.
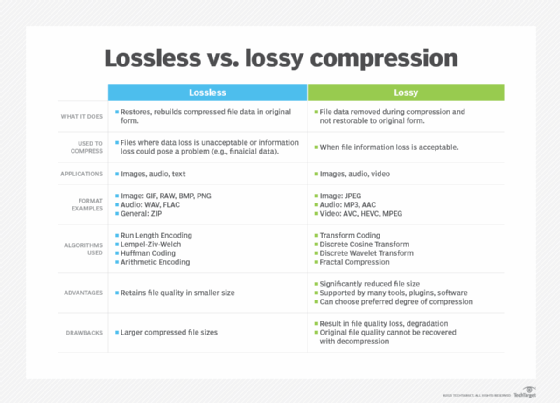
MP3 audio is a way to compress audio to use much less data and still sound good. MP3 is a lossy encoding because some data is discarded and not recoverable later. First, a modified discrete cosine transform and a fast Fourier transform technique are used to reduce the full audio data into smaller data representations of the original values. Then, a psychoacoustic model is used to remove data that would not be heard by the human ear, such as frequencies above the human hearing range or sounds too quiet to hear. This resulting representation of the remaining audio data is then allocated and encoded to fit the data requirements. After encoding, an MP3 file might only take about 1 MB per minute for good-quality music.

Almost any modern device can play an MP3 file. Computers and smartphones will have a built-in audio player that can play MP3s, as well as other optional software, such as iTunes, that can play and organize MP3 files. Most modern CD players can read and play MP3 files that have been burned to a CD. Likewise, most recent car entertainment systems can play MP3 files stored on a CD or USB storage.
MP3 files also contain ID3 tag information. This can contain metadata such as the song title, artist name, album title and year.
When to use MP3
These days, the MP3 format is best used where wide compatibility is desired and quality or efficiency are not important. This makes MP3s a good choice for recording voice memos or sending recordings over the internet.
When not to use MP3
Because MP3 is a lossy format, it shouldn't be used for archive or audio editing purposes. A lossless format such as WAV or Free Lossless Audio Codec, or FLAC, is a better choice for these needs.
Newer formats offer better audio characteristics at smaller file sizes. Where the playback device is known in these settings, such as a new smartphone, an embedded industrial playback device, a streaming service or audio files for a computer program, a new codec -- such as Advanced Audio Coding (AAC), Ogg Vorbis or Ogg Opus -- is more appropriate than MP3.
MP3 vs. MP4
Although MP3 and MP4 use similar file extensions, they usually refer to different things. MP3 is used for audio files, and MP4 is for video files.
MP3 was developed as an audio codec option for MPEG-1 video, or H.261. It could also be used for MPEG-2 video, or H.262. These combined video and audio files will often use the .mpg or .mpeg file extensions. Because it was the third layer, or type, of audio codec for the MPEG standard, it used the .mp3 file extension.
MP4 is a file container format developed for the MPEG-4 video standard. It will generally contain an HEVC , or H.265, video and AAC audio. An audio-only MP4 file will usually have the .m4a or .mp4 file extension.
History of MP3
Moving Picture Experts Group (MPEG) is a working group established by the International Organization for Standardization to set standards for audio and video media encoding. It began work on its first codec, MPEG-1, in 1988. The MPEG-1 standard was released in 1993; it contained three audio standards, or layers. They were extended by the MPEG-2 standard released in 1995. The MPEG-1 Audio Layer 3, shortened to MP3, was the most efficient but computationally complex standard. Most videos, including DVD video, used the simpler Layer 2 encoding.
MP3 found popularity as a standalone audio format. During this time, a single CD of uncompressed music would take up almost the entire hard drive of a typical home computer, so compression was essential.
Computer programs allowed home users to rip the audio from a CD and encode it to MP3 for storage. These MP3 files could then be decoded later and burned to an audio CD again for playback in any standard CD player.
The relatively small sizes of MP3 files allowed them to be shared over the internet. Even over the relatively slow dial-up internet of the time, an MP3 could be downloaded in a few minutes. This led to rampant sharing of MP3s on the internet. These were stored on central servers initially. Later, file-sharing and peer-to-peer services would facilitate users hosting and sending files to each other.

Copyright owners worked to prevent content from being shared. They would often sue the file-sharing services and occasionally users. Sony went so far as to put a rootkit on audio CDs that would infect any computer they were inserted into as a form of copy protection.
The MP3 format itself was protected by many patents owned by different companies. This made licensing its use confusing and led to legal disputes between companies. The LAME, or LAME Ain't an MP3 Encoder, implementation was a freely available reference that got around these restrictions by only distributing sample code that the user or a third party could compile themselves. All patents on MP3 expired by 2017, making it freely usable.
MP3s also made portable media players, sometimes called MP3 players, possible. The most popular of these was the Apple iPod. Credited as being one of the greatest consumer electronics devices ever made, it revitalized Apple in the public consciousness. Many other lower-cost MP3 players were developed, with other notable examples being the Microsoft Zune and devices made by Creative Labs.
Today, most people listen to MP3s directly on their smartphones or through their mobile devices on Bluetooth speakers.
Explore the differences between compression, deduplication and encryption. Learn about what differentiates memory and storage.
